On January 10, 2024, Ivanti issued a warning regarding two high-severity zero-day vulnerabilities (CVE-2023-46805 and CVE-2024-218871) in Ivanti Connect Secure VPN. These vulnerabilities allow for authentication bypass and command injection within the web components of Ivanti Connect Secure and Ivanti Policy Secure. Threat actors can exploit these vulnerabilities to gain unauthorized access to restricted resources by evading control checks. Furthermore, authenticated administrators have the ability to send specially crafted requests and execute arbitrary commands on the affected appliance.
However, conducting forensic analyses becomes challenging because Ivanti utilises a custom version of its kernel based on LILO (Linux loader) that integrates the loop-AES tool for encrypting its data partitions.
Ivanti Connect Secure, formerly known as Pulse Connect Secure, utilises loop-AES encryption to secure its data partitions. Three different AES keys can be found in the three different kernels associated with the current, rollback, and resets factory partitions. While this encryption mechanism enhances data security, it presents significant hurdles for forensic analysts attempting to conduct digital investigations. With attackers actively exploiting vulnerabilities in Ivanti Connect Secure, it becomes imperative for analysts to overcome these encryption barriers to effectively analyse incidents and mitigate threats.
Thanks to the publication and work carried out by NorthwaveSecurity, we have been able to create a tool that automatically attempts to recover the AES encryption keys contained in Ivanti Pulse Connect Secure kernels (using LILO BootLoader and loop-AES).
The tool operates on dumped and decompressed (with extract-vmlinux) Linux kernels extracted from unencrypted partitions. Leveraging memory signature patterns, it identifies the loop_setup_root function within the kernel. Upon successful detection, the tool retrieves XORed AES encryption keys and their corresponding XOR keys. It then applies XOR operations to recover the AES keys, presenting them in a format compatible with the « lilo-pulse-secure-decrypt tool/dsdecrypt » (made by NorthwaveSecurity), which can decrypt DATA partitions.
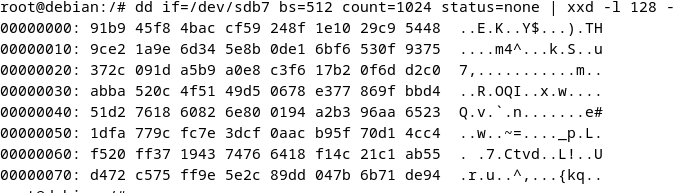
Below, an example of encrypted Ivanti Connect Secure volume. As expected, file & xxd commands display « data ».
If the tool runs successfully and manages to find the signature of the « loop_setup_root » function, you should get output similar to the screenshot below.
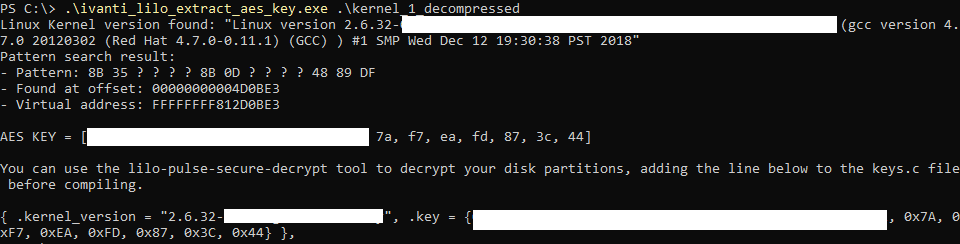
Once AES key recovered, we can compile dsdecrypt in order to decrypt our volume.

To find out more about reverse engineering of the AES encryption part of the Ivanti Kernel based on LILO / loop-AES, we invite you to consult the excellent article published by NorthWave-Cyber Security. You can find the link below in the external resources section.
You can download our tool on our GitHub repository at https://github.com/Intrinsec/ivanti_lilo_extract_aes_key
External Resources
- https://northwave-cybersecurity.com/whitepapers-articles/investigating-a-possible-ivanti-compromise
- https://github.com/NorthwaveSecurity/lilo-pulse-secure-decrypt
- https://github.com/torvalds/linux/blob/master/scripts/extract-vmlinux
- https://blog.maikxchd.com/comprehensive-ivanti-connect-secure-forensics-guide

