This article shares a method & tool developped by Intrinsec to reconstruct attack path using Microsoft Protection logs. Enjoy reading & hunting !
During incident response, CERT Intrinsec performs investigation so as to find indicators of compromise and reconstruct the attack path followed by the attackers. Amongst many approaches, it is possible to build that path by leveraging Microsoft Protection logs to spot tactics and techniques. These logs are named MPLog-*.log and are located under the directory C:\ProgramData\Microsoft\Windows Defender\Support\. They are operational logs and contain different information such as scanned resources and threats detected (command lines, binaries, etc). They are generated by the antimalware engine.
Link to the tool and instruction at the end of the article.
About log entries
CERT-Intrinsec has identified several input data types that can help during forensic investigations. The data listed below is not exhaustive and only relevant data is presented. The following tables provide information about log entries structures.
One-line entries
| Name of the log entry | Data Structure | Explanation |
| Lowfi | <DATE_TIME> Engine:command line reported as lowfi: <FULL_PATH_COMMAND_LINE> |
These log entries provided by this engine tracks command lines and is very useful to spot malicious activities. |
| EMS Scan | <DATE_TIME> Engine:EMS scan for process: <PROCESS_NAME> pid: <PID>, sigseq: <SIGSEQ>, sendMemoryScanReport: <SEND_MEMORY_SCAN_REPORT>, source: <SOURCE> |
The EMS engine that scan for processes is part of Windows Defender’s memory scanning engine. |
| Setting Original File name | <DATE_TIME> Engine:Setting original file name <ORIGINAL_FILE_NAME_FULL_PATH> for <FULL_PATH_FILENAME>, hr=<HR> |
This engine might be responsible for renaming entries in cache files. |
Command line reported as threat |
<DATE_TIME> Engine:command line reported as threat: <FULL_PATH_COMMAND> |
This engine identifies malicious command lines. |
| ProcessImageName* | <DATE_TIME> ProcessImageName: <PROCESS_NAME>, Pid: <PID>, TotalTime: <TOTAL_TIME>, Count: <COUNT>, MaxTime: <MAX_TIME>, MaxTimeFile: <MAX_TIME_FILE>, EstimatedImpact: <ESTIMATED_IMPACT>% |
These log entries provide information about estimated impact of scan on running processes. |
| DETECTION_ADD | <DATE_TIME> DETECTION_ADD#2 <THREAT_TYPE> <COMMAND_LINE> |
This entry logs threat detection and provides useful information such as threat type, command line, process id, etc. |
| DETECTIONEVENT MPSOURCE_SYSTEM | <DATE_TIME> DETECTIONEVENT MPSOURCE_SYSTEM <THREAT_TYPE> <COMMAND_LINE> |
This entry logs detection events and provides useful information, especially threat type and command line. |
* ProcessImageName fields description
| Field Name | Description |
| ProcessImageName | Process image name |
| Pid | ID of process |
| TotalTime | The cumulative duration in milliseconds spent in scans of files accessed by this process |
| Count | The number of scanned files accessed by this process |
| MaxTime | The duration in milliseconds in the longest single scan of a file accessed by this process |
| MaxTimeFile | The path of the file accessed by this process for which the longest scan of MaxTime duration was recorded |
| EstimatedImpact | The percentage of time spent in scans for files accessed by this process out of the period in which this process experienced scan activity |
Multi-line entries
Resource scan
The Resource Scan log entry can help identify malicious activities by providing information about resources identified as threats.
Begin Resource ScanScan ID:<SCAN_ID>Scan Source:<SCAN_SOURCE>Start Time:<START_TIME>End Time:<END_TIME>Explicit resource to scanResource Schema:<RESOURCE_SCHEMA>Resource Path:<RESOURCE_PATH>Result Count:<RESULT_COUNT>Threat Name:<THREAT_NAME>ID:<THREAT_NAME_ID>Severity:<SEVERITY>Number of Resources:<RESOURCE_NUMBER>Resource Schema:<RESOURCE_SCHEMA>Resource Path:<RESOURCE_PATH>Extended Info - SigSeq:<SIGSEQ>Extended Info - SigSha:<SIGSHA>End ScanBM Telemetry
The Behavior Monitoring module monitors file processes, file and registry changes, and other events on endpoints for suspicious and known malicious activities.
BEGIN BM telemetry
GUID:<GUID>
TelemetryName:<TELEMETRY_NAME: Behavior:Win32/[...]>
SignatureID:<SIGNATURE_ID_15-14_DIGITS>
ProcessID:<PID>
ProcessCreationTime:<TIMESTAMP>
SessionID:<SessionID>
CreationTime:<DATE_TIME>
ImagePath:<IMAGE_FULL_PATH>
ImagePathHash:<IMAGE_PATH_HASH>
END BM telemetry
Threat Actions
The Threat Actions module logs the different actions performed on threats (removal, quarantine, etc).
Beginning threat actions
Start time:<DATA_TIME>
Threat Name:<THREAT_NAME>
Threat ID:<THREAT_ID_10_DIGITS>
Action:<ACTION: Remove|Quarantine>
Resource action complete:<RESOURCE_ACTION_COMPLETE>
Schema:<SCHEMA: File|Folder>
Path:<FULL_PATH>
Threat ID:<THREAT_ID_10_DIGITS>
Resource refcount:<RESOURCE_REFCOUNT>
Result:<RESULT>
Resource action complete:<RESOURCE_ACTION_COMPLETE: Removal>
Schema:<SCHEMA>
Path:<FULL_PATH>
Threat ID:<THREAT_ID_10_DIGITS>
Resource refcount:<RESOURCE_REFCOUNT>
Result:<RESULT>
File owner:<ACCOUNT>
File cleaned/removed successfully
File Name:<FULL_PATH_FILE_NAME>
Action remove successful on file:<FULL_PATH_FILE_NAME>
Resource action complete:<RESOURCE_ACTION_COMPLETE: Removal>
Schema:<SCHEMA>
Path:<FULL_PATH>
Threat ID:<THREAT_ID_10_DIGITS>
Resource refcount:<RESOURCE_REFCOUNT>
Result:<RESULT>
Finished threat ID:<FINISHED_THREAT_ID_10_DIGITS>
Threat result:<THREAT_RESULT>
Threat status flags:<THREAT_STATUS_FLAGS>
Threat Effective RemovalPolicy:<THREAT_EFFECTIVE_REMOVALPOLICY>
Finished threat actions
Exclusion list
The Exclusion engine generates an exclusion list for the Real Time Protection module.
<DATE_TIME> [Exclusion] BEGIN: Starting to generate RTP exclusion list ...
<DATE_TIME> [Exclusion] <FULL_PATH_FILENAME_WITH_DRIVE_LETTER> -> <FULL_PATH_FILENAME_WITH_DEVICE_PATH>
[...]
<DATE_TIME> [Exclusion] <FULL_PATH_FILENAME> -> <FULL_PATH_FILENAME_WITH_DEVICE_PATH>
<DATE_TIME> [Exclusion] END: Successfully generated RTP exclusion list.
Mini-filter
With dataset analyzed, CERT Intrinsec has identified 5 different log entries for the Mini-filter engine Unsuccessful scan status, First scan on a volume, MpQueryLoadedDrivers called, OpenWithoutRead notification and Blocked File. The most relevant ones seem to be Unsuccessful scan status and Blocked File.
<DATE_TIME> [Mini-filter] Unsuccessful scan status: <FULL_PATH_FILENAME> Process: <PROCESS_NAME>, Status: <STATUS>, State: <STATE>, ScanRequest <SCANREQUEST>, FileId: <FILE_ID>, Reason: <REASON>, IoStatusBlockForNewFile: <IO_STATUS_BLOCK_FOR_NEW_FILE>, DesiredAccess: <DESIRED_ACCESS>, FileAttributes: <FILE_ATTRIBUTES>, ScanAttributes: <SCAN_ATTRIBUTES>, AccessStateFlags: <ACCESS_STATE_FLAGS>, BackingFileInfo: <BACKING_FILE_INFO>,
<DATE_TIME> [Mini-filter] First scan on a volume: <FULL_PATH_FILENAME>
<DATE_TIME> [Mini-filter] MpQueryLoadedDrivers called. bytesToCopy = <BYTES_TO_COPY>, ntStatus = <NT_STATUS>
<DATE_TIME> [Mini-filter] OpenWithoutRead notification (607, 10067, <FULL_PATH_FILENAME>) sent successfully.
<DATE_TIME> [Mini-filter] Blocked file: <FULL_PATH_FILENAME>. Process: <PROCESS_FULL_PATH_NAME>, Status: <STATUS>, State: <STATE>, ScanRequest <SCANREQUEST>, FileId: <FILEID>, Reason: <REASON>, IoStatusBlockForNewFile: <IO_STATUS_BLOCK_FOR_NEW_FILE>, DesiredAccess: <DESIRED_ACCESS>, FileAttributes: <FILE_ATTRIBUTES>, ScanAttributes: <SCAN_ATTRIBUTES>, AccessStateFlags: <ACCESS_STATE_FLAGS>, BackingFileInfo: <BACKING_FILE_INFO>,
Microsoft Protection Logs Parser
CERT Intrinsec uses Microsoft Protection logs when dealing with ransomwares or more advanced threats. In order to speed up the investigation and improve its forensic capabilities, it decided to write a script that extracts useful information from specific log entries within MPLog files. This parser is developed in Python and is looking for specific log patterns, that have been relevant during past investigations. It requires a folder containing log files and a folder that will store CSV output files thus created.
mplog_parser is available here : https://github.com/Intrinsec/mplog_parser.
You can find below two examples of MPLogs parser output, including lowfi entries and threat actions:
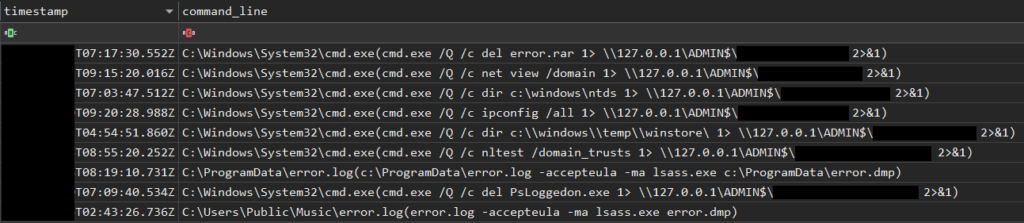
The MPLogs parser helps to identify malicious command lines from lowfi logs entries. You can see detections of discovery commands, tracks of lsass process dumping and the use of PsLoggedOn (SysInternals Tools).
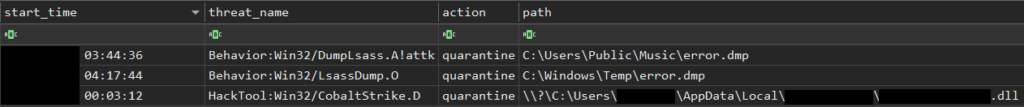
Threat action output identifies lsass process dumping activity and the presence of a malicious DLL, related to Cobalt Strike tools.
MITRE ATT&CK MATRIX
Microsoft Protection logs allows to spot many techniques used by adversaries, recording command lines or executed binaries. The following table sums up these techniques.
| Tactic | Technique | Technique ID |
| Execution | Command and Scripting Interpreter: Windows Command Shell | T1059.003 |
| Execution | Command and Scripting Interpreter: PowerShell | T1059.001 |
| Execution | Windows Management Instrumentation | T1047 |
| Persistence | Valid Accounts: Domain Accounts | T1078.002 |
| Defense Evasion | Impair Defenses: Disable or Modify Tools | T1562.001 |
| Defense Evasion | Indicator Removal on Host: File Deletion | T1070.004 |
| Credential Access | OS Credential Dumping: LSASS Memory | T1003.001 |
| Credential Access | OS Credential Dumping: NTDS | T1003.003 |
| Discovery | Account Discovery | T1087 |
| Discovery | Domain Trust Discovery | T1482 |
| Discovery | Network Share Discovery | T1135 |
| Discovery | System Information Discovery | T1082 |
| Discovery | File and Directory Discovery | T1083 |
| Discovery | Remote System Discovery | T1018 |
| Collection | Archive Collected Data: Archive via Utility | T1560.001 |
| Collection | Email Collection | T1114 |
| Collection | Data from Network Shared Drive | T1039 |
Sources
- Operational Logs : https://docs.microsoft.com/en-us/previous-versions/tn-archive/bb418913(v=technet.10)
- Information about
ProcessImageNamelog entry : https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/troubleshoot-performance-issues?view=o365-worldwide - CrowdStrike article about MPLog : https://www.crowdstrike.com/blog/how-to-use-microsoft-protection-logging-for-forensic-investigations/
Want to learn more about our Computer Emergency Response Team (CERT) ?

