Cyber threat intelligence
See what’s out of reach!
Discover our Cyber Threat Intelligence offer: a cyber threat intelligence and business intelligence offer tailored to the specific needs of companies. Structured around 4 complementary modules: Risk Anticipation – Asset Security Monitoring – Dataleak Detection – Brand Protection.
The aim of this offer is to anticipate and detect cyber threats linked to your exposure, helping you to improve your defense posture from tactical, operational and technical angles.
Cyber Threat Intelligence meets your objectives
Contextualized service
Protect your business from compromise, anticipate the costs associated with cyberthreats and benefit from a service tailored to your needs!
Active since 2014, our managed service is based on a unique technology, in constant development, feeding a unit of business intelligence analysts and technical experts covering both business needs and technical issues.
- Protect your business from cyber threats and compromises
- Combat data leaks (corporate, personal, etc.)
- Anticipate and avoid the major costs associated with a compromise
- Benefit from effective, contextualized monitoring
- Identify, characterize and analyze threats
- Benefit from continuous exposure mapping
Our Cyber Threat Intelligence offer
4 services – Complementary, modular & scalable.
By observing a broad spectrum of open sources, we help you identify your threat landscape and optimize your defense posture in the face of fraud, corporate or personal data leaks, attack preparations or the development of your shadow IT.
On a subscription basis, we help you build your Threat Intelligence program, implementing our approach via our portal and ongoing exchanges with an analyst dedicated to managing your Threat Intelligence service.
DataLeak Detection
Data leakage detection module in 4 steps.
Detection
Take stock of the data leaked and exposed on the Internet about your brands.
Analysis
Identify your critical points and the source of leaks :
- The volume of internal/strategic data publicly accessible on the Internet
- Employees’ good/bad practices regarding data confidentiality and protection of information assets
Alert
Alert you and provide you with the information you need to fully understand your risks
Remediation and protection
Following the assessment, our Cyber Threat Intelligence team will design a plan of recommendations tailored to your level of exposure and your challenges/needs.
Asset Security Monitoring
Module for controlling your Internet footprint.
The aim of our Asset Security Monitoring service is to reduce your available attack surface, and thus control your exposure to the Internet, by monitoring your perimeter assets and tracking their evolution. This involves :
- Discovery: Identifying your unknown surface (Shadow IT)
- Monitoring : Surveillance of your known attack surface and detection of compromised assets
Brand(s) Protection
Anti-fraud module.
Our anti-fraud service monitors an entity’s exposure to fraud.
To best protect your brands, we focus our research on 3 main areas:
- Anti-phishing: Monitoring of new domain registrations to anticipate phishing campaigns and prevent cyberquatting & typoquatting.
- Fight against fraud: On the different layers of the web (Deep, Dark & Surface) our Cellule analyzes your networks, platforms, black markets, in order to detect fraudulent markers relative to the targeted entity (Fight against digital fraud: counterfeiting, fraudulent sale of data, sharing of fraud schemes…).
- Fight against hacktivism: monitoring Social Networks and forums to detect smear campaigns that could have a cyber impact on your entities.
On the different layers of the web (Deep, Dark & Surface), our Watch Unit analyzes your networks, platforms, black markets, in order to detect markers relating to the targeted entity.
Risk Anticipation
Cyber risk prevention module.
Our Risk Anticipation service aims to keep you informed of the latest cyber threats and risks (IoC & TTP), from the generalist to the targeted, so that you can protect yourself against them:
- Anticipation of general risks : monitoring of vulnerabilities and cyber news (e.g. major attacks) and dispatch of regular short information bulletins.
- Anticipation of targeted risks: monitoring and drafting of an information note on a specific sector of activity.
Expertise OpenCTI OpenCTI expertise: technical and functional support in building a threat intelligence program around OpenCTI, and in deployment and use.
This module is available in English and/or French.
Would you like to be informed when a vulnerability is discovered in the software you use? In addition, discover our SSI Watch service.
I choose Intrinsec for my Cyber Threat Intelligence!
Highlights
Pure-player dimension: 360° expertise in cybersecurity to meet all your challenges and enhance your services
A team of intelligence officers with complementary profiles, drawing on the full range of our skills
OSINT & SOCMINT (Social Media Intelligence) investigation capacities developed on a day-to-day level for over 5 years
Our teams aremultilingual to understand your challenges, even abroad
Strong experience in detection & response:knowledge of threat actors and their methods, visibility of the latest attacks and vulnerabilities…
Our experience as a pure player offering an end-to-end approach to cybersecurity issues enables us to integrate this subject into a global strategy. The service we provide therefore takes into account all our experience (both operational and organizational), to offer pragmatic solutions and recommendations. By supporting structures of all sizes since 2014 on this theme, we have developed a practice that enables us to ensure rapid implementation. Service users receive their first alerts within the first few days of activation, and we support them throughout the service to build their Threat Intelligence program and make it evolve with their context.
I want more information!
Leave us a message describing your security needs, or contact us if you would like information about our Cyber Threat Intelligence services or our CTI modules: Dataleak Detection, Asset Security Monitoring, Brand Protection, Risk Anticipation.
Don’t forget to enter your e-mail address or telephone number so that we can contact you as soon as possible.
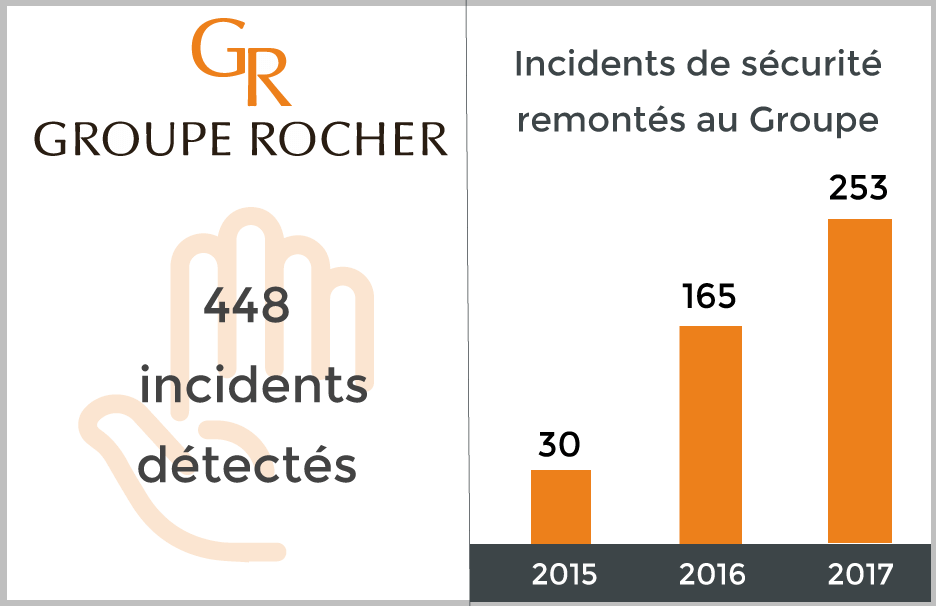
Customer case: Groupe Rocher
Frequently asked questions
How does the service work and is it intrusive?
What types of incidents does the service address?
- Preparing for attacks (DDOS, Phishing, Scams, Intrusion)
- Compromise of systems or applications
- Use of systems in other attacks
- Leakage of customer, business, corporate or personal data
- Exposure of sensitive systems
- Customer data capture
- Fraud
- Typosquatting
- Trademark infringement
- Cybercrime
Do you do vulnerability management and malware analysis?
- Vulnerability management involves collaboration with our SOC, which operates vulnerability management tools. We can scan systems detected as part of the service.
- Malware analysis is carried out in collaboration with our CERT: we can rapidly escalate analyses of artifacts, files, emails and any other malicious elements, and feed the results back into the marker stream.
Does the service address E-Reputation?
What sets you apart from your competitors?
- Experience accumulated since 2014, positioning us on tactical, operational and technical levels
- A 100% mastered technological approach, developed by Intrinsec, both in terms of analysis resources and Portal, the management and security as a service platform.
- A multilingual & multi-expertise team combining business intelligence and technical expertise in cybersecurity
We take the position of centralizing organizations’ Threat Intell approaches, bringing together under our management the contributions of several partners (E-Reputation, strategic Threat Intell, complementary geographical coverage, etc.) for organizations with advanced needs.
Expert opinion
Cybercrime Threat Landscape April 2023
Here is a retrospective of the major trends observed by Intrinsec's Cyber Threat Intelligence team regarding the month of April 2023. This cybercrime threat landscape analysis will particularily concentrate on : Decrease of ransomware attacks between March & April...
Cybercrime Threat Landscape March 2023
Cyber Threat Landscape 2022
Cybercrime Threat Landscape February 2023
Here is a retrospective of the major trends observed by Intrinsec's Cyber Threat Intelligence team regarding the month of February 2023. This threat landscape analysis will particularily concentrate on : - Fake claim of global payment services leader #Ingenico by...







