- Kerberos OPSEC: Offense & Detection Strategies for Red and Blue Team – Introduction
- Kerberos OPSEC: Offense & Detection Strategies for Red and Blue Team – Part 1 : Kerberoasting
- Kerberos OPSEC: Offense & Detection Strategies for Red and Blue Team – Part 2 : AS_REP Roasting
We are starting a series of articles in which we share a summary of the OPSEC practices to be taken into account on the red team side, and the detection strategies that can be put in place by SOC teams to detect certain advanced techniques based on the Kerberos protocol.
Red teaming exercises simulate adversaries in order to :
- identify compromise paths enabling access to sensitive assets;
- evaluate & improve existing detection and response systems and procedures.
In order to challenge the Blue Team, the Red Team must be discreet in achieving its objectives (e.g.: getting customer data, AWS tenant, Active Directory domain, etc.). Red Team operators must therefore master the tools and techniques they use, and be able to modify them to leave as few traces as possible.
The term OPSEC (Operations Security) is used to describe the difficulty with which the red team’s actions can be detected by the blue team.
Intrinsec’s RedTeam
Intrinsec’s RedTeam is dedicated to this activity, and uses its skills to perform Red Teaming exercises of varying lengths, from a few weeks to a few months, or in a more original setting through its « Trophy Hunter » model, to extend the exercise over a year and use new exploits and opportunities as they arise. The business leverages the work of the CTI team, shares common tools and invests significant R&D time around its methods, tools and technical means to achieve its goals. The team also frequently collaborates during Purple Teaming exercises with detection & response teams to improve the efficiency of detection resources or operational business practices.
What is Kerberos ?
Kerberos is one of the authentication systems available in Active Directory environments. This protocol enables users and machines to authenticate themselves on the network and access services in an authenticated way. Kerberos is based on the use of Ticket Granting Ticket (TGT) and Ticket Granting Service (TGS).
In this article, we won’t go into how the Kerberos protocol works. An explanation can be found on the following blogpost: https://beta.hackndo.com/kerberos/.
During our RedTeams, we come across situations where the use of attack techniques based on the Kerberos protocol are detected when carried out with known tools (e.g. impacket suite, Rubeus, etc.). We have adapted our techniques and tools to get under the Blue Team’s radar, and then extended our recommendations to improve our customers’ detection strategies.
Disclaimer:
- We will only be discussing the traces and effects of our actions in relation to Kerberos protocol techniques. Memory evasion, signature evasion, etc. will not be considered;
- This article is not aiming to explain attack techniques, nor recommendations for correcting configuration faults. Here, we concentrate on OPSEC considerations and detection strategies.
Kerberos attacks
Kerberos is subject to a number of interesting actions from an attacker’s point of view. A number of attacks and techniques can be carried out to exploit various scenarios such as:
- Kerberoasting and ASREPRoasting
- Golden Ticket/Silver/Diamond Tickets
- Delegation exploitation (constrained and unconstrained)
- Lateral movement
- Etc.
Supported encryption types
To date, Active Directory offers five possible encryption suites for encrypting ticket secrets (may be subject to changes in the future):
- DES_CBC_CRC
- DES_CBC_MD5
- RC4-HMAC-MD5 (enctype 23)
- AES128-CTS-HMAC-SHA1-96 (enctype 17) – with 4096 PBKDF2 HMAC-SHA1 rounds
- AES256-CTS-HMAC-SHA1-96 (enctype 18) – with 4096 PBKDF2 HMAC-SHA1 rounds
Since Windows 2008 R2, DES is disabled on all created accounts (but can be enabled for backward compatibility reasons). By default, the RC4_HMAC_MD5 algorithm is used for domain user accounts secret encryption (AES128 and AES256 can be enabled but are not enabled by default, for backward compatibility reasons), with the exception of the krbtgt account secret, used to encrypt TGT, which is encrypted by default in AES if the domain’s functional level is 2008 or higher (and its password has been changed after upgrading to 2008 or higher). Note that for domain computer accounts, AES is the default.
To demonstrate this, we will add an SPN to the GALAXY\Qi-Ra account:
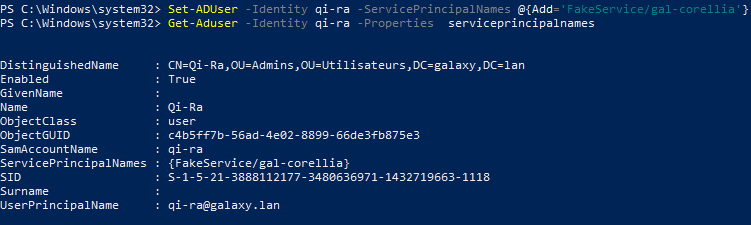
If we query the msDS-SupportedEncryptionTypes attribute, it will not appear:
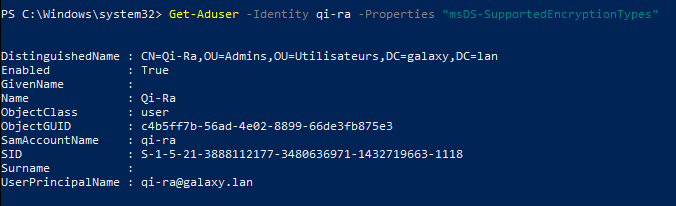
However, if we check in the advanced account options via the admin console, we can see that AES and DES are not enabled:
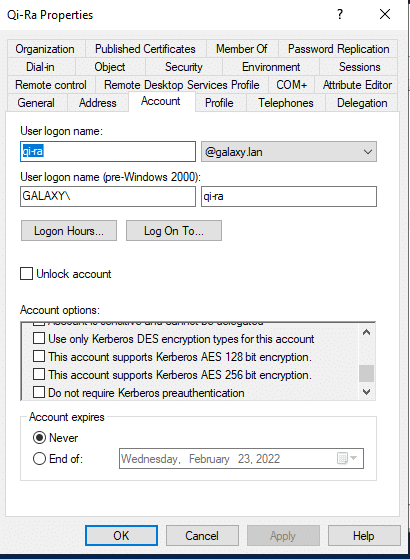
This means that RC4 is used by default. In order to use the most secure algorithms (AES128 and AES256), it is necessary to check the corresponding boxes, which can be seen in the advanced options of the GALAXY\R5-D4 account:
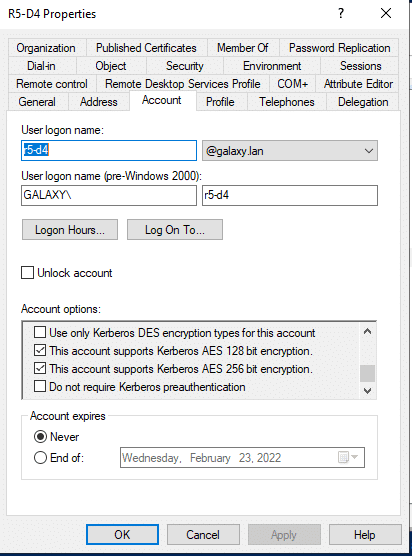
Thus, if we require the msDS-SupportedEncryptionTypes attribute:
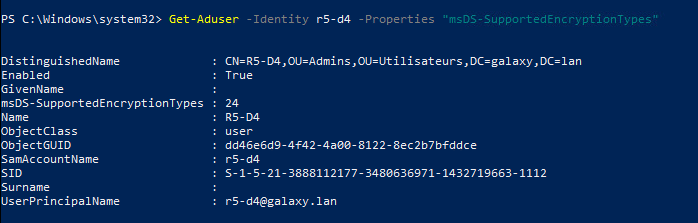
We can see that it is indeed present and that its value is 24, which corresponds to the support of:
- AES128
- AES256
If the account only supported AES256, the value would be 16.
So when we request a ticket for the service associated with this account, we’ll be able to choose the algorithm to be used, knowing that by default the highest proposed will be used, in this case AES256.
For more details, see the Microsoft official documentation.
Ticket options
Ticket requests have a number of possible options depending on the needs a user or application might have. These options are represented on 32 bits, each bit corresponding to the flag of a different option. The options are as follows:
| Bit | Flag |
| 0 | Reserved |
| 1 | Forwardable |
| 2 | Forwaded |
| 3 | Proxiable |
| 4 | Proxy |
| 5 | Allow Postdate |
| 6 | Postedated |
| 7 | Unused |
| 8 | Renewable |
| 9 | Unused |
| 10 | Unused |
| 11 | Optional Hardware Authentication |
| 12 | Unused |
| 13 | Unused |
| 14 | Canonicalize |
| 15 | Undefined |
| 16 | Undefined |
| 17 | Undefined |
| 18 | Undefined |
| 19 | Undefined |
| 20 | Undefined |
| 21 | Undefined |
| 22 | Undefined |
| 23 | Undefined |
| 24 | Undefined |
| 25 | Undefined |
| 26 | Disable Transited Check |
| 27 | Renewable Ok |
| 28 | Encrypt Ticket in Server Key |
| 29 | Undefined |
| 30 | Renew |
| 31 | Validate |
It’s important to know that ticket options are encoded in big endian, so the first bit of the string will be the first bit on the left.
In an ordinary ticket request, the following option string can be seen in the ticket request:
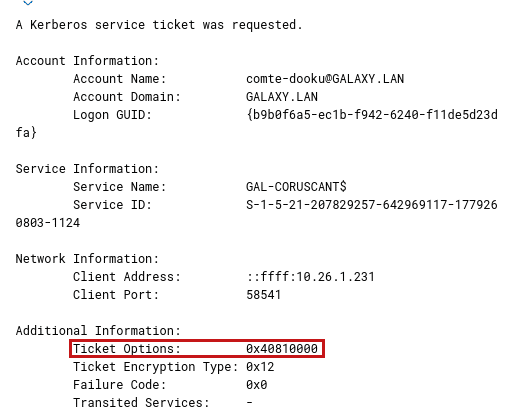
If we transform 0x40810000 into binary, it will give, in big endian:
01000000 10000001 00000000 00000000
Then read this from left to right to obtain the following options (starting from 0):
- 1 : Forwardable
- 8 : Renewable
- 15 : Canonicalize
For more details, check the corresponding RFC.
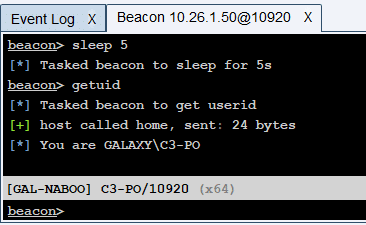
Demo context
Unless explicitly stated otherwise, the GALAXY.LAN domain user account we’ll be using for the demos is C3-PO. This user is not a local administrator on the victim machine (GAL-NABOO). The actions are performed from a Cobalt Strike agent running on this machine:
The Rubeus tool will be launched with the execute-assembly function (principle of Fork & Run) in the WerFault.exe sacrificial process:
We cleared the cache so that no tickets were initially present for the C3-PO user:
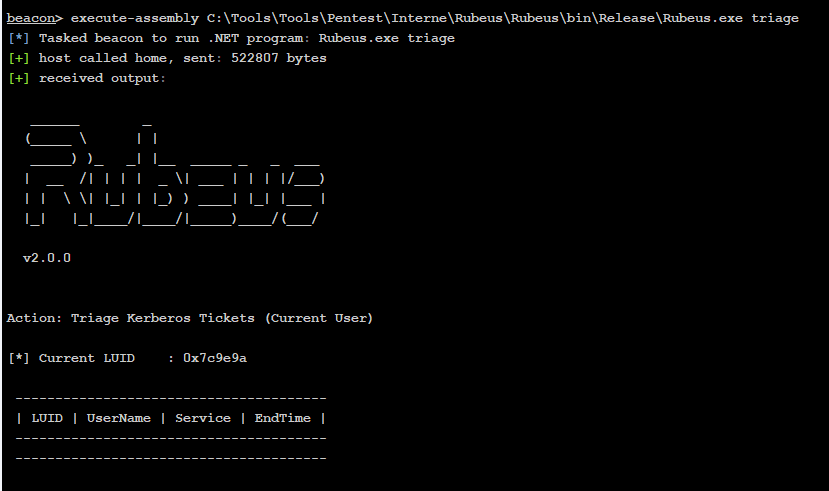
Log configurations
WARNING : The configurations mentionned here are only applicable to a lab environment as they can produce a very big amount of logs and thus can be difficult to analyze a in real scenario. They should be heavily modified to be useable in a production environment.
Domain controller
In order to enable the correct Active Directory logs, some configuration is necessary as they are not enabled by default.
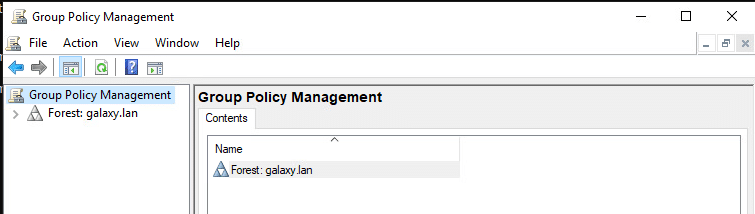
First of all, you need to activate the advanced auditing policy. To do this, in an administrator command prompt, type gpmc.msc, which will open the following window:
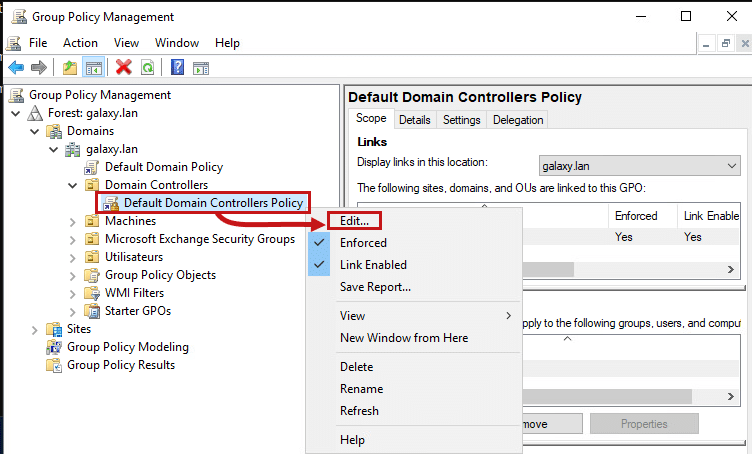
Then go to Group Policy Management -> Forest: <FOREST_NAME>-> Domains -> <DOMAIN_NAME> -> Domain Controllers and right-click on Default Domain Controllers Policy, then click on Edit:
It will open the following window:
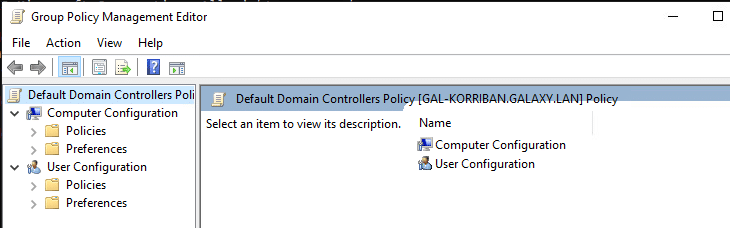
Then go to Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Advanced Audit Policy Configuration -> Audit Policies:
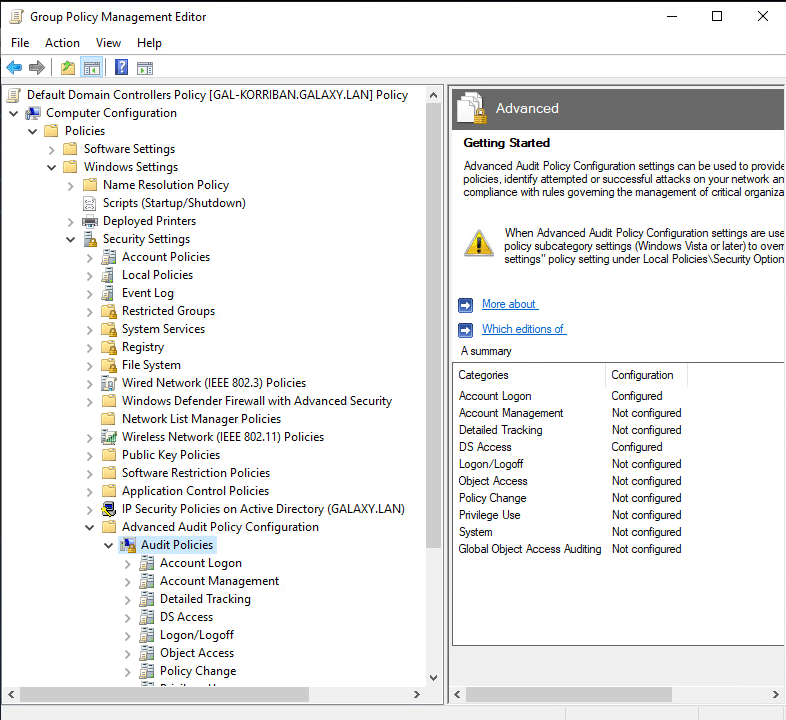
In Account Logon, set all options to Success and Failure:
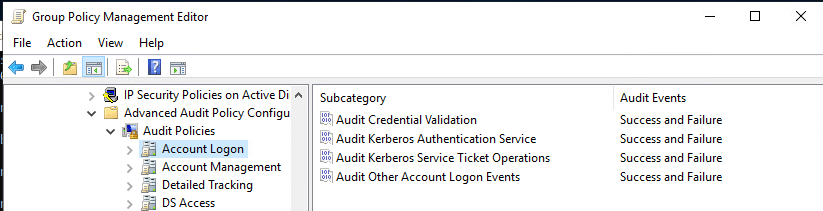
Same for DS Access:
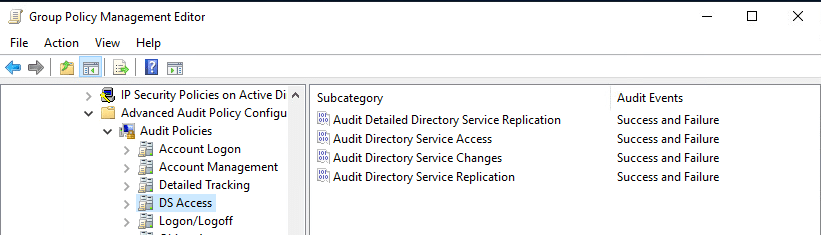
The next step is to modify the registry. In HKLM\SYSTEM\CurrentControlSet\ServicesNTDS\Diagnostics\, change the key 15 Field Engineering to 5 (verbose):
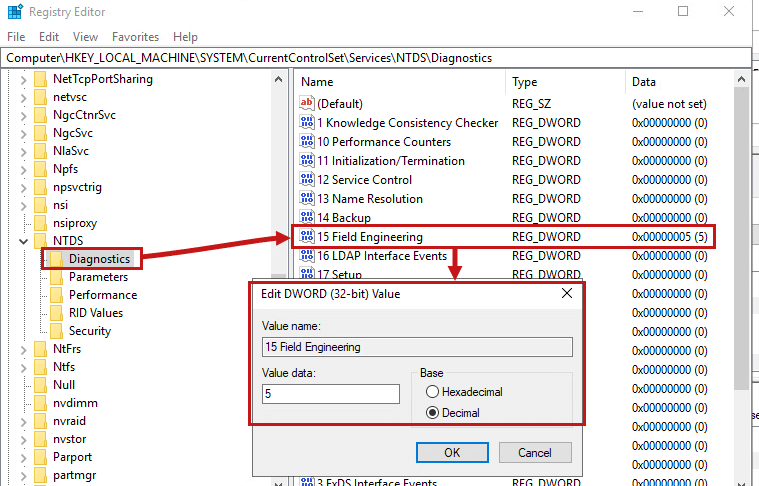
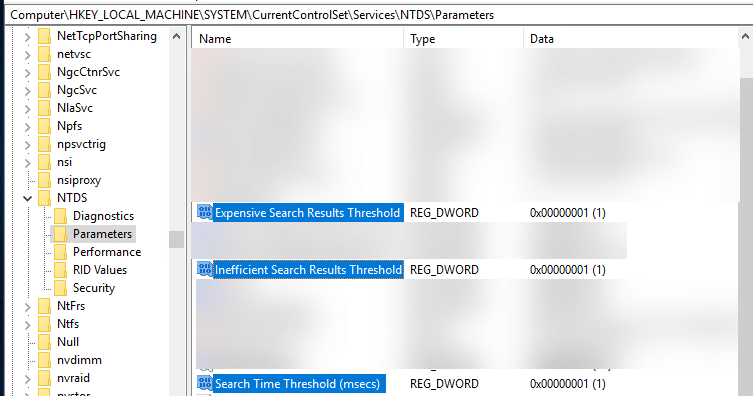
Then in HKLM\SYSTEM\CurrentControlSet\ServicesNT\Parameters\, add the following DWORDs:
- « Expensive Search Results Threshold » to 1
- « Inefficient Search Results Threshold » to 1
- « Search Time Threshold (msecs) » to 1
Sysmon
Here is the Sysmon configuration used in our lab:
<!-- NOTICE : This is a custom generated output of Sysmon-modular with higher verbosity -->
<!-- The log volume expected from this file is significantly larger than a more balanced log -->
<!-- the blind spots for this config are to be significantly less -->
<!-- for more information go to https://github.com/olafhartong/sysmon-modular/wiki -->
<!-- -->
<!-- //** ***// -->
<!-- ///#(** **%(/// -->
<!-- ((&&&** **&&&(( -->
<!-- (&&&** ,(((((((. **&&&( -->
<!-- ((&&**(((((//(((((((/**&&(( _____ __ __ -->
<!-- (&&///((////(((((((///&&( / ___/__ ___________ ___ ____ ____ ____ ___ ____ ____/ /_ __/ /___ ______ -->
<!-- &////(/////(((((/(////& \__ \/ / / / ___/ __ `__ \/ __ \/ __ \______/ __ `__ \/ __ \/ __ / / / / / __ `/ ___/ -->
<!-- ((// /////(///// /((( ___/ / /_/ (__ ) / / / / / /_/ / / / /_____/ / / / / / /_/ / /_/ / /_/ / / /_/ / / -->
<!-- &(((((#.///////// #(((((& /____/\__, /____/_/ /_/ /_/\____/_/ /_/ /_/ /_/ /_/\____/\__,_/\__,_/_/\__,_/_/ -->
<!-- &&&&((#///////((#((&&&& /____/ -->
<!-- &&&&(#/***//(#(&&&& -->
<!-- &&&&****///&&&& by Olaf Hartong -->
<!-- (& ,&. -->
<!-- .*&&*. -->
<!-- -->
<Sysmon schemaversion="4.60">
<HashAlgorithms>*</HashAlgorithms>
<!-- This now also determines the file names of the files preserved (String) -->
<CheckRevocation>False</CheckRevocation>
<!-- Setting this to true might impact performance -->
<DnsLookup>False</DnsLookup>
<!-- Disables lookup behavior, default is True (Boolean) -->
<ArchiveDirectory>Sysmon</ArchiveDirectory>
<!-- Sets the name of the directory in the C:\ root where preserved files will be saved (String)-->
<EventFiltering>
<!-- Event ID 1 == Process Creation - Excludes -->
<RuleGroup groupRelation="or">
<ProcessCreate onmatch="exclude">
<Rule groupRelation="and">
<Image condition="end with">AcroRd32.exe</Image>
<CommandLine condition="contains any">/CR;channel=</CommandLine>
</Rule>
<Rule groupRelation="or">
<Image condition="end with">C:\Program Files (x86)\Adobe\Acrobat DC\Acrobat\AcroCEF\AcroCEF.exe</Image>
<ParentImage condition="end with">C:\Program Files (x86)\Common Files\Adobe\AdobeGCClient\AGSService.exe</ParentImage>
<Image condition="end with">C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe</Image>
<Image condition="end with">C:\Program Files (x86)\Adobe\Acrobat DC\Acrobat\LogTransport2.exe</Image>
</Rule>
<Image condition="end with">C:\Program Files (x86)\Adobe\Adobe Creative Cloud\ACC\Creative Cloud.exe</Image>
<ParentImage condition="end with">C:\Program Files (x86)\Adobe\Adobe Creative Cloud\ACC\Creative Cloud.exe</ParentImage>
<ParentImage condition="end with">C:\Program Files (x86)\Adobe\Adobe Creative Cloud\CCXProcess\CCXProcess.exe</ParentImage>
<ParentImage condition="end with">C:\Program Files (x86)\Adobe\Adobe Creative Cloud\CoreSync\CoreSync.exe</ParentImage>
<Image condition="end with">C:\Windows\SysWOW64\Macromed\Flash\FlashPlayerUpdateService.exe</Image>
<Image condition="end with">C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe</Image>
<ParentImage condition="end with">C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe</ParentImage>
<Image condition="end with">C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\armsvc.exe</Image>
<Image condition="end with">C:\Program Files (x86)\Adobe\Acrobat DC\Acrobat\AdobeCollabSync.exe</Image>
<Image condition="end with">C:\Program Files (x86)\Common Files\Adobe\Adobe Desktop Common\HEX\Adobe CEF Helper.exe</Image>
<Image condition="end with">C:\Program Files (x86)\Common Files\Adobe\AdobeGCClient\AdobeGCClient.exe</Image>
<Image condition="end with">C:\Program Files (x86)\Common Files\Adobe\OOBE\PDApp\P6\adobe_licutil.exe</Image>
<Image condition="end with">C:\Program Files (x86)\Common Files\Adobe\OOBE\PDApp\P7\adobe_licutil.exe</Image>
<ParentImage condition="end with">C:\Program Files (x86)\Common Files\Adobe\OOBE\PDApp\P7\adobe_licutil.exe</ParentImage>
<Image condition="end with">C:\Program Files (x86)\Common Files\Adobe\OOBE\PDApp\UWA\updaterstartuputility.exe</Image>
<ParentImage condition="is">C:\Program Files (x86)\Common Files\Adobe\OOBE\PDApp\UWA\updaterstartuputility.exe</ParentImage>
<ParentCommandLine condition="is">"C:\Program Files\Microsoft Monitoring Agent\Agent\MonitoringHost.exe" -Embedding</ParentCommandLine>
<Rule groupRelation="and">
<ParentImage condition="is">"C:\Program Files\Microsoft Monitoring Agent\Agent\MonitoringHost.exe"</ParentImage>
<CommandLine condition="is">C:\Windows\system32\cscript.exe" /nologo "MonitorKnowledgeDiscovery.vbs</CommandLine>
</Rule>
<ParentImage condition="end with">C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\vpnagent.exe</ParentImage>
<CommandLine condition="begin with">C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe</CommandLine>
<Image condition="is">C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe</Image>
<Image condition="is">C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe</Image>
<Image condition="is">C:\Windows\Microsoft.Net\Framework64\v3.0\WPF\PresentationFontCache.exe</Image>
<Image condition="is">C:\Windows\Microsoft.Net\Framework64\v3.0\WPF\PresentationFontCache.exe</Image>
<ParentCommandLine condition="contains">C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ngentask.exe</ParentCommandLine>
<ParentImage condition="is">C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe</ParentImage>
<ParentImage condition="is">C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ngentask.exe</ParentImage>
<ParentImage condition="is">C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe</ParentImage>
<ParentImage condition="is">C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngentask.exe</ParentImage>
<ParentImage condition="is">C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngentask.exe</ParentImage>
<Image condition="begin with">C:\Program Files\NVIDIA Corporation\</Image>
<Image condition="begin with">C:\Program Files\Realtek\</Image>
<ParentImage condition="end with">C:\Program Files\Realtek\Audio\HDA\RtkAudioService64.exe</ParentImage>
<Image condition="end with">C:\Program Files (x86)\Dropbox\Update\DropboxUpdate.exe</Image>
<ParentImage condition="end with">C:\Program Files (x86)\Dropbox\Update\DropboxUpdate.exe</ParentImage>
<Image condition="is">C:\Program Files\ESET\ESET Nod32 Antivirus\ekrn.exe</Image>
<CommandLine condition="begin with">"C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=</CommandLine>
<CommandLine condition="begin with">"C:\Program Files\Google\Chrome\Application\chrome.exe" --type=</CommandLine>
<Image condition="begin with">C:\Program Files (x86)\Google\Update\</Image>
<ParentImage condition="begin with">C:\Program Files (x86)\Google\Update\</ParentImage>
<ParentImage condition="is">C:\Program Files (x86)\RES Software\Workspace Manager\pfwsmgr.exe</ParentImage>
<ParentImage condition="is">C:\Program Files (x86)\RES Software\Workspace Manager\respesvc64.exe</ParentImage>
<ParentImage condition="is">C:\Program Files (x86)\Ivanti\Workspace Control\pfwsmgr.exe</ParentImage>
<ParentImage condition="is">C:\Program Files (x86)\RES Software\Workspace Manager\ResPesvc64.exe</ParentImage>
<ParentImage condition="is">C:\Program Files\RES Software\Workspace Manager\respesvc.exe</ParentImage>
<ParentImage condition="is">C:\Program Files\Ivanti\Workspace Control\ResPesvc.exe</ParentImage>
<Image condition="is">C:\Program Files\Malwarebytes\Anti-Malware\mbam.exe</Image>
<Image condition="is">C:\Program Files\Malwarebytes\Anti-Malware\mbamservice.exe</Image>
<Image condition="is">C:\Program Files\Malwarebytes\Anti-Malware\mbamtray.exe</Image>
<Image condition="is">C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeC2RClient.exe</Image>
<ParentImage condition="end with">C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeClickToRun.exe</ParentImage>
<ParentImage condition="is">C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeC2RClient.exe</ParentImage>
<Image condition="is">C:\Program Files (x86)\Microsoft Office\Office16\MSOSYNC.EXE</Image>
<Image condition="is">C:\Program Files\Common Files\Microsoft Shared\OfficeSoftwareProtectionPlatform\OSPPSVC.EXE</Image>
<CommandLine condition="begin with">"C:\Program Files\Mozilla Firefox\plugin-container.exe" --channel</CommandLine>
<CommandLine condition="begin with">"C:\Program Files (x86)\Mozilla Firefox\plugin-container.exe" --channel</CommandLine>
<Image condition="contains all"> C:\Users\;\AppData\Local\Microsoft\OneDrive;\FileCoAuth.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Sophos Anti-Virus\Web Intelligence\swi_service.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Sophos Anti-Virus\Web Control\swc_service.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Sophos System Protection\ssp.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Remote Management System\RouterNT.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\AutoUpdate\ALsvc.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Sophos Anti-Virus\SAVAdminService.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Remote Management System\ManagementAgentNT.exe</Image>
<Image condition="begin with">C:\Program Files\Splunk\bin\</Image>
<ParentImage condition="is">C:\Program Files\Splunk\bin\splunkd.exe</ParentImage>
<ParentImage condition="is">C:\Program Files\Splunk\bin\splunk.exe</ParentImage>
<Image condition="begin with">D:\Program Files\Splunk\bin\</Image>
<ParentImage condition="is">D:\Program Files\Splunk\bin\splunkd.exe</ParentImage>
<ParentImage condition="is">D:\Program Files\Splunk\bin\splunk.exe</ParentImage>
<Image condition="begin with">C:\Program Files\SplunkUniversalForwarder\bin\</Image>
<ParentImage condition="is">C:\Program Files\SplunkUniversalForwarder\bin\splunkd.exe</ParentImage>
<ParentImage condition="is">C:\Program Files\SplunkUniversalForwarder\bin\splunk.exe</ParentImage>
<Image condition="begin with">D:\Program Files\SplunkUniversalForwarder\bin\</Image>
<ParentImage condition="is">D:\Program Files\SplunkUniversalForwarder\bin\splunkd.exe</ParentImage>
<ParentImage condition="is">D:\Program Files\SplunkUniversalForwarder\bin\splunk.exe</ParentImage>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k appmodel -s StateRepository</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k appmodel</CommandLine>
<CommandLine condition="is">C:\WINDOWS\system32\svchost.exe -k appmodel -p -s tiledatamodelsvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k camera -s FrameServer</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k dcomlaunch -s LSM</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k dcomlaunch -s PlugPlay</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k defragsvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k devicesflow -s DevicesFlowUserSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k imgsvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localService -s EventSystem</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localService -s bthserv</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localService -s nsi</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localService -s w32Time</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localServiceAndNoImpersonation</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localServiceNetworkRestricted -s Dhcp</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localServiceNetworkRestricted -s EventLog</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localServiceNetworkRestricted -s TimeBrokerSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localServiceNetworkRestricted -s WFDSConMgrSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localServiceNetworkRestricted</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localServiceAndNoImpersonation -s SensrSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localServiceNoNetwork</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -p -s WPDBusEnum</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -p -s fhsvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -s DeviceAssociationService</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -s NcbService</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -s SensorService</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -s TabletInputService</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -s UmRdpService</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -s WPDBusEnum</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted -s WdiSystemHost</CommandLine>
<CommandLine condition="is">C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s WdiSystemHost</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted</CommandLine>
<CommandLine condition="is">C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s wlidsvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -p -s ncaSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s BDESVC</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s BITS</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s CertPropSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s DsmSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s Gpsvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s ProfSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s SENS</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s SessionEnv</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s Themes</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs -s Winmgmt</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k networkService -p -s DoSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k networkService -s Dnscache</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k networkService -s LanmanWorkstation</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k networkService -s NlaSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k networkService -s TermService</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k networkService</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k networkServiceNetworkRestricted</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k rPCSS</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k secsvcs</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k swprv</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k unistackSvcGroup</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k utcsvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k wbioSvcGroup</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k werSvcGroup</CommandLine>
<CommandLine condition="is">C:\WINDOWS\System32\svchost.exe -k wsappx -p -s ClipSVC</CommandLine>
<CommandLine condition="is">C:\WINDOWS\system32\svchost.exe -k wsappx -p -s AppXSvc</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k wsappx -s ClipSVC</CommandLine>
<CommandLine condition="is">C:\Windows\system32\svchost.exe -k wsappx</CommandLine>
<ParentCommandLine condition="is">C:\Windows\system32\svchost.exe -k netsvcs</ParentCommandLine>
<ParentCommandLine condition="is">C:\Windows\system32\svchost.exe -k localSystemNetworkRestricted</ParentCommandLine>
<Image condition="is">C:\Program Files\Trend Micro\Deep Security Agent\ds_monitor.exe</Image>
<Image condition="is">C:\Program Files\Trend Micro\Deep Security Agent\dsa.exe</Image>
<Image condition="is">C:\Program Files\Trend Micro\Deep Security Agent\dsuam.exe</Image>
<Image condition="is">C:\Program Files\Trend Micro\Deep Security Agent\Notifier.exe</Image>
<Image condition="is">C:\Program Files\Trend Micro\Deep Security Agent\lib\Patch.exe</Image>
<Image condition="is">C:\Program Files (x86)\Trend Micro\BM\TMBMSRV.exe</Image>
<Image condition="is">C:\Program Files (x86)\Trend Micro\OfficeScan Client\TmopExtIns32.exe</Image>
<Image condition="is">C:\Program Files (x86)\Trend Micro\OfficeScan Client\TmExtIns.exe</Image>
<Image condition="is">C:\Program Files (x86)\Trend Micro\OfficeScan Client\TmListen.exe</Image>
<Image condition="begin with">C:\Program Files\Windows Defender\</Image>
<Image condition="is">C:\Windows\system32\MpSigStub.exe</Image>
<Image condition="begin with">C:\Windows\SoftwareDistribution\Download\Install\AM_</Image>
<Image condition="is">C:\Program Files\Microsoft Security Client\MpCmdRun.exe</Image>
<CommandLine condition="begin with">C:\Windows\system32\DllHost.exe /Processid</CommandLine>
<CommandLine condition="is">C:\Windows\system32\SearchIndexer.exe /Embedding</CommandLine>
<Image condition="end with">C:\Windows\System32\CompatTelRunner.exe</Image>
<Image condition="is">C:\Windows\System32\MusNotification.exe</Image>
<Image condition="is">C:\Windows\System32\MusNotificationUx.exe</Image>
<Image condition="is">C:\Windows\System32\audiodg.exe</Image>
<Image condition="is">C:\Windows\System32\conhost.exe</Image>
<Image condition="is">C:\Windows\System32\powercfg.exe</Image>
<Image condition="is">C:\Windows\System32\wbem\WmiApSrv.exe</Image>
<Image condition="is">C:\Windows\System32\wermgr.exe</Image>
<Image condition="is">C:\Windows\SysWOW64\wermgr.exe</Image>
<Image condition="is">C:\Windows\system32\sppsvc.exe</Image>
<IntegrityLevel condition="is">AppContainer</IntegrityLevel>
<ParentCommandLine condition="begin with">%%SystemRoot%%\system32\csrss.exe ObjectDirectory=\Windows</ParentCommandLine>
<ParentImage condition="is">C:\Windows\system32\SearchIndexer.exe</ParentImage>
</ProcessCreate>
</RuleGroup>
<!-- Event ID 2 == File Creation Time - Excludes -->
<RuleGroup groupRelation="or">
<FileCreateTime onmatch="exclude">
<Image condition="end with">AppData\Local\Google\Chrome\Application\chrome.exe</Image>
<Image condition="end with">Root\VFS\ProgramFilesX86\Google\Chrome\Application\chrome.exe</Image>
<Image condition="image">OneDrive.exe</Image>
<Image condition="contains">setup</Image>
<Image condition="end with">slack.exe</Image>
<Image condition="end with">AppData\Local\Microsoft\Teams\current\Teams.exe</Image>
</FileCreateTime>
</RuleGroup>
<!-- Event ID 3 == Network Connection - Excludes -->
<RuleGroup groupRelation="or">
<NetworkConnect onmatch="exclude">
<Image condition="end with">AppData\Roaming\Dropbox\bin\Dropbox.exe</Image>
<Image condition="end with">winlogbeat.exe</Image>
<Image condition="end with">packetbeat.exe</Image>
<Image condition="is">C:\Program Files\ESET\ESET Nod32 Antivirus\ekrn.exe</Image>
<Image condition="image">OneDrive.exe</Image>
<Image condition="image">OneDriveStandaloneUpdater.exe</Image>
<Image condition="end with">ownCloud\owncloud.exe</Image>
<Image condition="is">C:\Program Files\Palo Alto Networks\Traps\cyserver.exe</Image>
<Rule groupRelation="and">
<Protocol condition="is">udp</Protocol>
<DestinationPort condition="is">3389</DestinationPort>
</Rule>
<Image condition="is">C:\Program Files (x86)\Sophos\Sophos Anti-Virus\Web Intelligence\swi_service.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\AutoUpdate\ALsvc.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Remote Management System\RouterNT.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Sophos Anti-Virus\Web Control\swc_service.exe</Image>
<Image condition="is">C:\Program Files (x86)\Sophos\Sophos Anti-Virus\Web Intelligence\swi_service.exe</Image>
<Image condition="is">C:\Program Files\Sophos\Sophos Network Threat Protection\bin\SntpService.exe</Image>
<Image condition="end with">AppData\Roaming\Spotify\Spotify.exe</Image>
<Image condition="end with">AppData\Local\SynologyDrive\SynologyDrive.app\bin\cloud-drive-ui.exe</Image>
<Image condition="end with">AppData\Local\SynologyDrive\SynologyDrive.app\bin\cloud-drive-daemon.exe</Image>
<Image condition="is">C:\Program files (x86)\Trend Micro\OfficeScan Client\tmlisten.exe</Image>
<Image condition="is">C:\Program Files (x86)\Trend Micro\BM\TMBMSRV.exe</Image>
<DestinationHostname condition="end with">.windowsupdate.microsoft.com</DestinationHostname>
<DestinationHostname condition="end with">.windowsupdate.com</DestinationHostname>
<DestinationHostname condition="end with">wustat.windows.com</DestinationHostname>
<DestinationHostname condition="end with">go.microsoft.com</DestinationHostname>
<DestinationHostname condition="end with">.update.microsoft.com</DestinationHostname>
<DestinationHostname condition="end with">download.microsoft.com</DestinationHostname>
<DestinationHostname condition="end with">microsoft.com.akadns.net</DestinationHostname>
<DestinationHostname condition="end with">microsoft.com.nsatc.net</DestinationHostname>
</NetworkConnect>
</RuleGroup>
<!-- Event ID 5 == Process Terminated - Includes -->
<RuleGroup groupRelation="or">
<ProcessTerminate onmatch="include" />
</RuleGroup>
<!-- Event ID 6 == Driver Loaded - Excludes -->
<RuleGroup groupRelation="or">
<!--Default to log all and exclude only valid signed Microsoft or Intel drivers-->
<DriverLoad onmatch="exclude">
<Rule groupRelation="and">
<Signature condition="begin with">Intel </Signature>
<SignatureStatus condition="is">Valid</SignatureStatus>
</Rule>
<Rule groupRelation="and">
<Signature condition="contains">Microsoft</Signature>
<SignatureStatus condition="is">Valid</SignatureStatus>
</Rule>
</DriverLoad>
</RuleGroup>
<!-- Event ID 7 == Image Loaded - Excludes -->
<RuleGroup groupRelation="or">
<ImageLoad onmatch="exclude">
<Rule groupRelation="and">
<Image condition="is">C:\Windows\System32\cscript.exe</Image>
<OriginalFileName condition="is">scrobj.dll</OriginalFileName>
</Rule>
<Rule groupRelation="and">
<Image name="technique_id=T1137,technique_name=Office Application Startup" condition="end with">VSTOInstaller.exe</Image>
<ImageLoaded condition="begin with">C:\Windows\</ImageLoaded>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all"> C:\Users\;\AppData\Local\Microsoft\OneDrive;\FileCoAuth.exe</Image>
<ImageLoaded condition="contains all">C:\Users\;\AppData\Local\Microsoft\OneDrive\;\FileSyncTelemetryExtensions.dll</ImageLoaded>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all"> C:\Users\;\AppData\Local\Microsoft\OneDrive;\FileCoAuth.exe</Image>
<ImageLoaded condition="contains all">C:\Users\;\AppData\Local\Microsoft\OneDrive\;\FileCoAuthLib.dll</ImageLoaded>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all"> C:\Users\;\AppData\Local\Microsoft\OneDrive;\FileCoAuth.exe</Image>
<ImageLoaded condition="contains all">C:\Users\;\AppData\Local\Microsoft\OneDrive\;\OneDriveTelemetryStable.dll</ImageLoaded>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all"> C:\Users\;\AppData\Local\Microsoft\OneDrive;\FileCoAuth.exe</Image>
<ImageLoaded condition="contains all">C:\Users\;\AppData\Local\Microsoft\OneDrive\;\vcruntime140.dll</ImageLoaded>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all"> C:\Users\;\AppData\Local\Microsoft\OneDrive;\FileCoAuth.exe</Image>
<ImageLoaded condition="contains all">C:\Users\;\AppData\Local\Microsoft\OneDrive\;\UpdateRingSettings.dll</ImageLoaded>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all"> C:\Users\;\AppData\Local\Microsoft\OneDrive;\FileCoAuth.exe</Image>
<ImageLoaded condition="contains all">C:\Users\;\AppData\Local\Microsoft\OneDrive\;\LoggingPlatform.dll</ImageLoaded>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all"> C:\Users\;\AppData\Local\Microsoft\OneDrive;\FileCoAuth.exe</Image>
<ImageLoaded condition="contains all">C:\Users\;\AppData\Local\Microsoft\OneDrive\;\FileCoAuth.exe</ImageLoaded>
</Rule>
</ImageLoad>
</RuleGroup>
<!-- Event ID 8 == CreateRemoteThread - Excludes -->
<RuleGroup groupRelation="or">
<!--Default to log all and exclude a few common processes-->
<CreateRemoteThread onmatch="exclude">
<SourceImage condition="is">C:\Windows\System32\svchost.exe</SourceImage>
<SourceImage condition="is">C:\Windows\System32\wininit.exe</SourceImage>
<SourceImage condition="is">C:\Windows\System32\csrss.exe</SourceImage>
<SourceImage condition="is">C:\Windows\System32\services.exe</SourceImage>
<SourceImage condition="is">C:\Windows\System32\winlogon.exe</SourceImage>
<SourceImage condition="is">C:\Windows\System32\audiodg.exe</SourceImage>
<Rule groupRelation="and">
<SourceImage condition="is">C:\Windows\System32\dwm.exe</SourceImage>
<TargetImage condition="is">C:\Windows\System32\csrss.exe</TargetImage>
</Rule>
<TargetImage condition="end with">Google\Chrome\Application\chrome.exe</TargetImage>
<SourceImage condition="is">C:\Windows\System32\wbem\WmiPrvSE.exe</SourceImage>
</CreateRemoteThread>
</RuleGroup>
<!-- Event ID 9 == RawAccessRead - Includes -->
<RuleGroup groupRelation="or">
<RawAccessRead onmatch="include" />
</RuleGroup>
<!-- Event ID 10 == ProcessAccess - Excludes -->
<RuleGroup groupRelation="or">
<ProcessAccess onmatch="exclude">
<SourceImage condition="is">C:\Program Files\Adobe\Adobe Creative Cloud Experience\libs\node.exe</SourceImage>
<SourceImage condition="contains all">C:\Program Files;\Common Files\Adobe\AdobeGCClient\AGMService.exe</SourceImage>
<SourceImage condition="is">C:\Program Files (x86)\Adobe\Acrobat DC\Acrobat\Acrobat.exe</SourceImage>
<SourceImage condition="is">C:\Program Files (x86)\Adobe\Acrobat DC\Acrobat\AcroCEF\AcroCEF.exe</SourceImage>
<SourceImage condition="is">C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARMHelper.exe</SourceImage>
<SourceImage condition="is">C:\Program Files\Adobe\Adobe Photoshop 2021\Photoshop.exe</SourceImage>
<TargetImage condition="begin with">C:\Program Files\Autodesk\Autodesk Desktop App</TargetImage>
<TargetImage condition="begin with">C:\Program Files (x86)\Autodesk\Autodesk Desktop App</TargetImage>
<SourceImage condition="is">C:\Windows\CarbonBlack\cb.exe</SourceImage>
<SourceImage condition="contains all">C:\Program Files\Cisco\AMP\;sfc.exe</SourceImage>
<SourceImage condition="contains all">C:\Users\;\AppData\Local\Citrix\ICA Client\receiver\Receiver.exe</SourceImage>
<SourceImage condition="is">C:\Program Files (x86)\Citrix\ICA Client\Receiver\Receiver.exe</SourceImage>
<SourceImage condition="is">c:\Program Files\Couchbase\Server\bin\sigar_port.exe</SourceImage>
<SourceImage condition="contains all">C:\Program Files;\FireEye\xagt\xagt.exe</SourceImage>
<SourceImage condition="is">C:\Program Files (x86)\Ivanti\Workspace Control\cpushld.exe</SourceImage>
<SourceImage condition="is">C:\Program Files (x86)\RES Software\Workspace Manager\cpushld.exe</SourceImage>
<SourceImage condition="is">C:\Program Files\Ivanti\Workspace Control\cpushld.exe</SourceImage>
<SourceImage condition="is">C:\Program Files\RES Software\Workspace Manager\cpushld.exe</SourceImage>
<SourceImage condition="end with">wmiprvse.exe</SourceImage>
<SourceImage condition="end with">GoogleUpdate.exe</SourceImage>
<SourceImage condition="end with">LTSVC.exe</SourceImage>
<SourceImage condition="end with">taskmgr.exe</SourceImage>
<SourceImage condition="end with">VBoxService.exe</SourceImage>
<SourceImage condition="end with">vmtoolsd.exe</SourceImage>
<SourceImage condition="end with">\Citrix\System32\wfshell.exe</SourceImage>
<SourceImage condition="is">C:\Windows\System32\lsm.exe</SourceImage>
<SourceImage condition="end with">Microsoft.Identity.AadConnect.Health.AadSync.Host.exe</SourceImage>
<SourceImage condition="begin with">C:\Program Files (x86)\Symantec\Symantec Endpoint Protection</SourceImage>
<GrantedAccess>0x1000</GrantedAccess>
<GrantedAccess>0x1400</GrantedAccess>
<GrantedAccess>0x101400</GrantedAccess>
<GrantedAccess>0x101000</GrantedAccess>
<SourceImage condition="is">C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\mfeesp.exe</SourceImage>
<SourceImage condition="is">C:\Program Files\McAfee\Agent\x86\macompatsvc.exe</SourceImage>
<SourceImage condition="contains all">C:\Users\;\AppData\Local\Microsoft\OneDrive\StandaloneUpdater\OneDriveSetup.exe</SourceImage>
<SourceImage condition="is">C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE</SourceImage>
<SourceImage condition="is">C:\Program Files\PowerToys\modules\KeyboardManager\KeyboardManagerEngine\PowerToys.KeyboardManagerEngine.exe</SourceImage>
<Rule groupRelation="and">
<SourceImage condition="contains all">C:\Users\;\AppData\Local\Microsoft\Teams\current\Teams.exe</SourceImage>
<TargetImage condition="contains all">C:\Users\;\AppData\Local\Microsoft\Teams\current\Teams.exe</TargetImage>
</Rule>
<SourceImage condition="is">C:\Program Files\Microsoft Security Client\MsMpEng.exe</SourceImage>
<SourceImage condition="is">C:\Program Files\Windows Defender\MsMpEng.exe</SourceImage>
<SourceImage condition="contains all">C:\ProgramData\Microsoft\Windows Defender\Platform\;\MsMpEng.exe</SourceImage>
<SourceImage condition="is">C:\Program Files (x86)\Mobatek\MobaXterm\MobaXterm.exe</SourceImage>
<SourceImage condition="is">C:\Program Files\Palo Alto Networks\Traps\cyserver.exe</SourceImage>
<SourceImage condition="is">C:\Program Files\Qualys\QualysAgent\QualysAgent.exe</SourceImage>
<SourceImage condition="is">C:\Program Files (x86)\Razer Chroma SDK\bin\RzSDKService.exe</SourceImage>
<SourceImage condition="is">C:\WINDOWS\CCM\CcmExec.exe</SourceImage>
<SourceImage condition="is">C:\Program Files\Splunk\bin\splunkd.exe</SourceImage>
<SourceImage condition="is">C:\Program Files (x86)\VMware\VMWare Player\vmware-authd.exe</SourceImage>
<SourceImage condition="is">C:\Program Files (x86)\VMware\VMware Workstation\vmware-authd.exe</SourceImage>
<SourceImage condition="is">C:\Program Files\WinZip\FAHWindow64.exe</SourceImage>
</ProcessAccess>
</RuleGroup>
<!-- Event ID 11 == FileCreate - Excludes -->
<RuleGroup groupRelation="or">
<FileCreate onmatch="exclude">
<Image condition="is">C:\Program Files (x86)\Dell\CommandUpdate\InvColPC.exe</Image>
<Image condition="is">C:\Windows\system32\igfxCUIService.exe</Image>
<Image condition="is">C:\Program Files (x86)\Ivanti\Workspace Control\pfwsmgr.exe</Image>
<Image condition="is">C:\Program Files (x86)\RES Software\Workspace Manager\pfwsmgr.exe</Image>
<Image condition="is">C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeC2RClient.exe</Image>
<Image condition="is">C:\Windows\System32\smss.exe</Image>
<Image condition="is">C:\Windows\system32\CompatTelRunner.exe</Image>
<Image condition="is">C:\Windows\system32\wbem\WMIADAP.EXE</Image>
<TargetFilename condition="begin with">C:\Windows\System32\DriverStore\Temp\</TargetFilename>
<TargetFilename condition="begin with">C:\Windows\System32\wbem\Performance\</TargetFilename>
<TargetFilename condition="end with">WRITABLE.TST</TargetFilename>
<TargetFilename condition="contains">\AppData\Roaming\Microsoft\Windows\Recent\</TargetFilename>
<TargetFilename condition="begin with">C:\$WINDOWS.~BT\Sources\SafeOS\SafeOS.Mount\</TargetFilename>
<Image condition="begin with">C:\WINDOWS\winsxs\amd64_microsoft-windows</Image>
<Image condition="is">c:\Program Files\Microsoft Security Client\MsMpEng.exe</Image>
<Rule groupRelation="and">
<Image condition="image">Outlook.exe</Image>
<TargetFilename condition="contains">Roaming\Microsoft\Outlook\Outlook.xml</TargetFilename>
</Rule>
<Image condition="is">c:\windows\system32\provtool.exe</Image>
<Image condition="is">C:\WINDOWS\CCM\CcmExec.exe</Image>
<TargetFilename condition="begin with">C:\Windows\CCM</TargetFilename>
<TargetFilename condition="begin with">C:\Windows\System32\Tasks\Microsoft\Windows\PLA\FabricTraces</TargetFilename>
<TargetFilename condition="begin with">C:\Windows\System32\Tasks\Microsoft\Windows\SoftwareProtectionPlatform\SvcRestartTask</TargetFilename>
<TargetFilename condition="begin with">C:\Windows\System32\Tasks\Microsoft\Windows\Customer Experience Improvement Program\Server\ServerRoleUsageCollector</TargetFilename>
<TargetFilename condition="begin with">C:\Windows\System32\Tasks\Microsoft\Windows\Customer Experience Improvement Program\Server\ServerCeipAssistant</TargetFilename>
</FileCreate>
</RuleGroup>
<!-- Event ID 12,13,14 == RegObject added/deleted, RegValue Set, RegObject Renamed - Excludes -->
<RuleGroup groupRelation="or">
<RegistryEvent onmatch="exclude">
<Image condition="is">C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\aciseposture.exe</Image>
<Image condition="is">C:\Program Files (x86)\Cisco\Cisco AnyConnect Secure Mobility Client\vpnagent.exe</Image>
<Image condition="is">C:\Program Files\Cylance\Optics\CyOptics.exe</Image>
<Image condition="is">C:\Program Files\Cylance\Desktop\CylanceSvc.exe</Image>
<TargetObject condition="end with">Toolbar\WebBrowser</TargetObject>
<TargetObject condition="end with">Toolbar\WebBrowser\ITBar7Height</TargetObject>
<TargetObject condition="end with">Toolbar\ShellBrowser\ITBar7Layout</TargetObject>
<TargetObject condition="end with">Internet Explorer\Toolbar\Locked</TargetObject>
<TargetObject condition="end with">ShellBrowser</TargetObject>
<Image condition="is">C:\Program Files (x86)\Ivanti\Workspace Control\pfwsmgr.exe</Image>
<Image condition="is">C:\Program Files\RES Software\Workspace Manager\pfwsmgr.exe</Image>
<Image condition="begin with">C:\Program Files (x86)\Kaspersky Lab\Kaspersky Internet Security </Image>
<Image condition="begin with">C:\Program Files\Kaspersky Lab\Kaspersky Internet Security </Image>
<Image condition="is">C:\Program Files\McAfee\Endpoint Encryption Agent\MfeEpeHost.exe</Image>
<Image condition="is">C:\Program Files\McAfee\Endpoint Security\Adaptive Threat Protection\mfeatp.exe</Image>
<Image condition="is">C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\mfeesp.exe</Image>
<Image condition="is">C:\Program Files\Common Files\McAfee\Engine\AMCoreUpdater\amupdate.exe</Image>
<Image condition="is">C:\Program Files\McAfee\Agent\masvc.exe</Image>
<Image condition="is">C:\Program Files\McAfee\Agent\x86\mfemactl.exe</Image>
<Image condition="is">C:\Program Files\McAfee\Agent\x86\McScript_InUse.exe</Image>
<Image condition="is">C:\Program Files\McAfee\Agent\x86\macompatsvc.exe</Image>
<Image condition="is">C:\Program Files\McAfee\Endpoint Security\Threat Prevention\mfeensppl.exe</Image>
<Image condition="begin with">C:\Program Files\Common Files\McAfee\Engine\scanners</Image>
<Image condition="is">C:\Program Files\Common Files\McAfee\AVSolution\mcshield.exe</Image>
<Image condition="is">C:\Program Files\ownCloud\owncloud.exe</Image>
<Image condition="is">C:\Program Files (x86)\ownCloud\owncloud.exe</Image>
<Rule groupRelation="and">
<Image condition="image">svchost.exe</Image>
<TargetObject condition="begin with">HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks</TargetObject>
</Rule>
<Image condition="begin with">C:\Program Files\SentinelOne\Sentinel Agent</Image>
<Image condition="is">System</Image>
<Rule groupRelation="and">
<Image condition="is">C:\Program Files\VMware\VMware Tools\vmtoolsd.exe</Image>
<TargetObject condition="is">HKLM\System\CurrentControlSet\Services\Tcpip\Parameters</TargetObject>
</Rule>
<Image condition="is">C:\Program Files (x86)\Webroot\WRSA.exe</Image>
<Image condition="is">C:\Program Files\WIDCOMM\Bluetooth Software\btwdins.exe</Image>
<TargetObject condition="end with">HKLM\SYSTEM\CurrentControlSet\Control\Lsa\Audit</TargetObject>
<TargetObject condition="end with">HKLM\SYSTEM\CurrentControlSet\Control\Lsa\Audit\AuditPolicy</TargetObject>
<TargetObject condition="end with">HKLM\SYSTEM\CurrentControlSet\Control\Lsa\Audit\PerUserAuditing\System</TargetObject>
<TargetObject condition="end with">HKLM\SYSTEM\CurrentControlSet\Control\Lsa\SspiCache</TargetObject>
<TargetObject condition="end with">HKLM\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\Domains</TargetObject>
<TargetObject condition="end with">HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\Audit</TargetObject>
<TargetObject condition="contains">\OpenWithProgids</TargetObject>
<TargetObject condition="end with">\OpenWithList</TargetObject>
<TargetObject condition="end with">\UserChoice</TargetObject>
<TargetObject condition="end with">\UserChoice\ProgId</TargetObject>
<TargetObject condition="end with">\UserChoice\Hash</TargetObject>
<TargetObject condition="end with">\OpenWithList\MRUList</TargetObject>
<TargetObject condition="end with">} 0xFFFF</TargetObject>
<Image condition="end with">Office\root\integration\integrator.exe</Image>
<Image condition="is">C:\WINDOWS\system32\backgroundTaskHost.exe</Image>
<Image condition="is">C:\Program Files\Common Files\Microsoft Shared\ClickToRun\OfficeClickToRun.exe</Image>
<Image condition="is">C:\Program Files\Windows Defender\MsMpEng.exe</Image>
<Image condition="is">C:\Windows\SystemApps\Microsoft.Windows.Cortana_cw5n1h2txyewy\SearchUI.exe</Image>
<Image condition="is">C:\Program Files\Microsoft Application Virtualization\Client\AppVClient.exe</Image>
<TargetObject condition="end with">\CurrentVersion\App Paths</TargetObject>
<TargetObject condition="end with">\CurrentVersion\Image File Execution Options</TargetObject>
<TargetObject condition="end with">\CurrentVersion\Shell Extensions\Cached</TargetObject>
<TargetObject condition="end with">\CurrentVersion\Shell Extensions\Approved</TargetObject>
<TargetObject condition="end with">}\PreviousPolicyAreas</TargetObject>
<TargetObject condition="contains">\Control\WMI\Autologger\</TargetObject>
<TargetObject condition="end with">HKLM\SYSTEM\CurrentControlSet\Services\UsoSvc\Start</TargetObject>
<TargetObject condition="end with">\Lsa\OfflineJoin\CurrentValue</TargetObject>
<TargetObject condition="end with">\Components\TrustedInstaller\Events</TargetObject>
<TargetObject condition="end with">\Components\TrustedInstaller</TargetObject>
<TargetObject condition="end with">\Components\Wlansvc</TargetObject>
<TargetObject condition="end with">\Components\Wlansvc\Events</TargetObject>
<TargetObject condition="begin with">HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\</TargetObject>
<TargetObject condition="end with">\Directory\shellex</TargetObject>
<TargetObject condition="end with">\Directory\shellex\DragDropHandlers</TargetObject>
<TargetObject condition="end with">\Drive\shellex</TargetObject>
<TargetObject condition="end with">\Drive\shellex\DragDropHandlers</TargetObject>
<TargetObject condition="contains">_Classes\AppX</TargetObject>
<TargetObject condition="begin with">HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\WINEVT\Publishers\</TargetObject>
<TargetObject condition="is">HKLM\SOFTWARE\Policies\Microsoft\SystemCertificates\Root\Certificates</TargetObject>
<Image condition="is">C:\Windows\SystemApps\Microsoft.Windows.Cortana_cw5n1h2txyewy\SearchUI.exe</Image>
<Image condition="begin with">C:\$WINDOWS.~BT\</Image>
<TargetObject condition="is">HKLM\System\CurrentControlSet\Services\Tcpip\Parameters</TargetObject>
<Rule groupRelation="and">
<Image condition="is">C:\Windows\system32\lsass.exe</Image>
<TargetObject condition="contains">HKLM\System\CurrentControlSet\Services</TargetObject>
</Rule>
<TargetObject condition="end with">\services\clr_optimization_v2.0.50727_32\Start</TargetObject>
<TargetObject condition="end with">\services\clr_optimization_v2.0.50727_64\Start</TargetObject>
<TargetObject condition="end with">\services\clr_optimization_v4.0.30319_32\Start</TargetObject>
<TargetObject condition="end with">\services\clr_optimization_v4.0.30319_64\Start</TargetObject>
<TargetObject condition="end with">\services\DeviceAssociationService\Start</TargetObject>
<TargetObject condition="end with">\services\BITS\Start</TargetObject>
<TargetObject condition="end with">\services\TrustedInstaller\Start</TargetObject>
<TargetObject condition="end with">\services\tunnel\Start</TargetObject>
<TargetObject condition="end with">\services\UsoSvc\Start</TargetObject>
</RegistryEvent>
</RuleGroup>
<!-- Event ID 15 == FileStream Created - Excludes -->
<RuleGroup groupRelation="or">
<FileCreateStreamHash onmatch="exclude" />
</RuleGroup>
<!-- Event ID 17,18 == PipeEvent. Log Named pipe created & Named pipe connected - Excludes -->
<RuleGroup groupRelation="or">
<PipeEvent onmatch="exclude">
<Rule groupRelation="and">
<Image condition="contains all">C:\Program Files;\Common Files\Adobe\ARM\1.0\AdobeARM.exe</Image>
<PipeName condition="begin with">\32B6B37A-4A7D-4e00-95F2-</PipeName>
<PipeName condition="end with">thsnYaVieBoda</PipeName>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all">C:\Program Files;\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe</Image>
<PipeName condition="begin with">\com.adobe.reader.rna.;\mojo</PipeName>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all">C:\Program Files;\Common Files\Adobe\AdobeGCClient\AGMService.exe</Image>
<PipeName condition="begin with">\gc_pipe_</PipeName>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all">C:\Program Files;\Common Files\Adobe\Creative Cloud Libraries\libs\node.exe</Image>
<PipeName condition="begin with">\uv\</PipeName>
</Rule>
<Image condition="is">"C:\Program Files\Microsoft Monitoring Agent\Agent\MonitoringHost.exe"</Image>
<Rule groupRelation="and">
<Image condition="contains all"> C:\Users\;\AppData\Local\Programs\Call Manager\Call Manager.exe</Image>
<PipeName condition="begin with">\crashpad_;\mojo.;\uv\</PipeName>
</Rule>
<Image condition="contains all">C:\Program Files;\Citrix\ICA Client\SelfServicePlugin\SelfService.exe</Image>
<Image condition="contains all">C:\Program Files;\Citrix\ICA Client\Receiver\Receiver.exe</Image>
<Image condition="contains all">C:\Program Files;\Citrix\ICA Client\wfcrun32.exe</Image>
<Image condition="contains all">C:\Program Files;\Citrix\ICA Client\concentr.exe</Image>
<Image condition="contains all">C:\Users\;\AppData\Local\Citrix\ICA Client\receiver\Receiver.exe</Image>
<Image condition="contains all">C:\Users\;\AppData\Local\Citrix\ICA Client\SelfServicePlugin\SelfService.exe</Image>
<Image condition="contains all">C:\Program Files;\FireEye\xagt\xagt.exe</Image>
<Rule groupRelation="and">
<Image condition="contains all">C:\Program Files;\Google\Update\Install\;setup.exe</Image>
<PipeName condition="begin with">\crashpad_</PipeName>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all">C:\Program Files;\Google\Chrome\Application\chrome.exe</Image>
<PipeName condition="begin with">\mojo.</PipeName>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all">C:\Program Files;\Google\Chrome\Application\;\Installer\chrmstp.exe</Image>
<PipeName condition="begin with">\crashpad_</PipeName>
</Rule>
<PipeName condition="begin with">\Vivisimo Velocity</PipeName>
<Rule groupRelation="and">
<Image condition="contains all">C:\Program Files;\Microsoft\Edge\Application\msedge.exe</Image>
<PipeName condition="begin with">\LOCAL\mojo.</PipeName>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all">C:\Program Files;\Microsoft\Edge\Application\msedge.exe</Image>
<PipeName condition="begin with">\LOCAL\chrome.sync.</PipeName>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all">C:\Program Files;\Microsoft\Edge\Application\msedge.exe</Image>
<PipeName condition="begin with">\LOCAL\crashpad_</PipeName>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all">C:\Program Files;\Microsoft Office\root\Office16\OUTLOOK.EXE</Image>
<PipeName condition="is">\MsFteWds</PipeName>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all">C:\Users\;\AppData\Local\Microsoft\Teams\current\Teams.exe</Image>
<PipeName condition="begin with">\mojo.</PipeName>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all">C:\Users\;\AppData\Local\Microsoft\Teams\current\Teams.exe</Image>
<PipeName condition="begin with">\chrome.sync.</PipeName>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all">C:\Program Files;\Mozilla Firefox\firefox.exe</Image>
<PipeName condition="begin with">\cubeb-pipe-</PipeName>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all">C:\Program Files;\Mozilla Firefox\firefox.exe</Image>
<PipeName condition="begin with">\chrome.</PipeName>
</Rule>
<Rule groupRelation="and">
<Image condition="contains all">C:\Program Files;\Mozilla Firefox\firefox.exe</Image>
<PipeName condition="begin with">\gecko-crash-server-pipe.</PipeName>
</Rule>
<PipeName condition="is">\SQLLocal\MSSQLSERVER</PipeName>
<PipeName condition="is">\SQLLocal\INSTANCE01</PipeName>
<PipeName condition="is">\SQLLocal\SQLEXPRESS</PipeName>
<PipeName condition="is">\SQLLocal\COMMVAULT</PipeName>
<PipeName condition="is">\SQLLocal\RTCLOCAL</PipeName>
<PipeName condition="is">\SQLLocal\RTC</PipeName>
<PipeName condition="is">\SQLLocal\TMSM</PipeName>
<Image condition="is">Program Files (x86)\Microsoft SQL Server\110\DTS\binn\dtexec.exe</Image>
<Image condition="end with">PostgreSQL\9.6\bin\postgres.exe</Image>
<PipeName condition="contains">\pgsignal_</PipeName>
<Image condition="is">Program Files\Qlik\Sense\Engine\Engine.exe</Image>
<Image condition="contains all">C:\Program Files;\Qualys\QualysAgent\QualysAgent.exe</Image>
<Image condition="end with">Program Files\SplunkUniversalForwarder\bin\splunkd.exe</Image>
<Image condition="end with">Program Files\SplunkUniversalForwarder\bin\splunk.exe</Image>
<Image condition="end with">Program Files\SplunkUniversalForwarder\bin\splunk-MonitorNoHandle.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\CMAgent\OfcCMAgent.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\web\service\ofcservice.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\Web\Service\DbServer.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\web\service\verconn.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\WEB_OSCE\WEB\CGI\cgiOnClose.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\WEB_OSCE\WEB\CGI\cgiRqHotFix.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\LWCS\LWCSService.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\WSS\iCRCService.exe</Image>
<Image condition="end with">Program Files\Trend\SPROTECT\x64\tsc.exe</Image>
<Image condition="end with">Program Files\Trend\SPROTECT\x64\tsc64.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\web\service\osceintegrationservice.exe</Image>
<Image condition="end with">Program Files (x86)\Trend Micro\OfficeScan\PCCSRV\web\service\OfcLogReceiverSvc.exe</Image>
<PipeName condition="is">\Trend Micro OSCE Command Handler Manager</PipeName>
<PipeName condition="is">\Trend Micro OSCE Command Handler2 Manager</PipeName>
<PipeName condition="is">\Trend Micro Endpoint Encryption ToolBox Command Handler Manager</PipeName>
<PipeName condition="is">\OfcServerNamePipe</PipeName>
<PipeName condition="is">\ntapvsrq</PipeName>
<PipeName condition="is">\srvsvc</PipeName>
<PipeName condition="is">\wkssvc</PipeName>
<PipeName condition="is">\lsass</PipeName>
<PipeName condition="is">\winreg</PipeName>
<PipeName condition="is">\spoolss</PipeName>
<PipeName condition="contains">Anonymous Pipe</PipeName>
<Image condition="is">c:\windows\system32\inetsrv\w3wp.exe</Image>
</PipeEvent>
</RuleGroup>
<!-- Event ID 19,20,21, == WmiEvent. Log all WmiEventFilter, WmiEventConsumer, WmiEventConsumerToFilter activity - Excludes -->
<RuleGroup groupRelation="or">
<WmiEvent onmatch="exclude" />
</RuleGroup>
<!-- Event ID 22 == DNS Queries and their results Excludes -->
<RuleGroup groupRelation="or">
<!--Default to log all and exclude a few common processes-->
<DnsQuery onmatch="exclude">
<QueryName condition="end with">.1rx.io</QueryName>
<QueryName condition="end with">.2mdn.net</QueryName>
<QueryName condition="end with">.adadvisor.net</QueryName>
<QueryName condition="end with">.adap.tv</QueryName>
<QueryName condition="end with">.addthis.com</QueryName>
<QueryName condition="end with">.adform.net</QueryName>
<QueryName condition="end with">.adnxs.com</QueryName>
<QueryName condition="end with">.adroll.com</QueryName>
<QueryName condition="end with">.adrta.com</QueryName>
<QueryName condition="end with">.adsafeprotected.com</QueryName>
<QueryName condition="end with">.adsrvr.org</QueryName>
<QueryName condition="end with">.advertising.com</QueryName>
<QueryName condition="end with">.amazon-adsystem.com</QueryName>
<QueryName condition="end with">.amazon-adsystem.com</QueryName>
<QueryName condition="end with">.analytics.yahoo.com</QueryName>
<QueryName condition="end with">.aol.com</QueryName>
<QueryName condition="end with">.betrad.com</QueryName>
<QueryName condition="end with">.bidswitch.net</QueryName>
<QueryName condition="end with">.casalemedia.com</QueryName>
<QueryName condition="end with">.chartbeat.net</QueryName>
<QueryName condition="end with">.cnn.com</QueryName>
<QueryName condition="end with">.convertro.com</QueryName>
<QueryName condition="end with">.criteo.com</QueryName>
<QueryName condition="end with">.criteo.net</QueryName>
<QueryName condition="end with">.crwdcntrl.net</QueryName>
<QueryName condition="end with">.demdex.net</QueryName>
<QueryName condition="end with">.domdex.com</QueryName>
<QueryName condition="end with">.dotomi.com</QueryName>
<QueryName condition="end with">.doubleclick.net</QueryName>
<QueryName condition="end with">.doubleverify.com</QueryName>
<QueryName condition="end with">.emxdgt.com</QueryName>
<QueryName condition="end with">.exelator.com</QueryName>
<QueryName condition="end with">.google-analytics.com</QueryName>
<QueryName condition="end with">.googleadservices.com</QueryName>
<QueryName condition="end with">.googlesyndication.com</QueryName>
<QueryName condition="end with">.googletagmanager.com</QueryName>
<QueryName condition="end with">.googlevideo.com</QueryName>
<QueryName condition="end with">.gstatic.com</QueryName>
<QueryName condition="end with">.gvt1.com</QueryName>
<QueryName condition="end with">.gvt2.com</QueryName>
<QueryName condition="end with">.ib-ibi.com</QueryName>
<QueryName condition="end with">.jivox.com</QueryName>
<QueryName condition="end with">.mathtag.com</QueryName>
<QueryName condition="end with">.moatads.com</QueryName>
<QueryName condition="end with">.moatpixel.com</QueryName>
<QueryName condition="end with">.mookie1.com</QueryName>
<QueryName condition="end with">.myvisualiq.net</QueryName>
<QueryName condition="end with">.netmng.com</QueryName>
<QueryName condition="end with">.nexac.com</QueryName>
<QueryName condition="end with">.openx.net</QueryName>
<QueryName condition="end with">.optimizely.com</QueryName>
<QueryName condition="end with">.outbrain.com</QueryName>
<QueryName condition="end with">.pardot.com</QueryName>
<QueryName condition="end with">.phx.gbl</QueryName>
<QueryName condition="end with">.pinterest.com</QueryName>
<QueryName condition="end with">.pubmatic.com</QueryName>
<QueryName condition="end with">.quantcount.com</QueryName>
<QueryName condition="end with">.quantserve.com</QueryName>
<QueryName condition="end with">.revsci.net</QueryName>
<QueryName condition="end with">.rfihub.net</QueryName>
<QueryName condition="end with">.rlcdn.com</QueryName>
<QueryName condition="end with">.rubiconproject.com</QueryName>
<QueryName condition="end with">.scdn.co</QueryName>
<QueryName condition="end with">.scorecardresearch.com</QueryName>
<QueryName condition="end with">.serving-sys.com</QueryName>
<QueryName condition="end with">.sharethrough.com</QueryName>
<QueryName condition="end with">.simpli.fi</QueryName>
<QueryName condition="end with">.sitescout.com</QueryName>
<QueryName condition="end with">.smartadserver.com</QueryName>
<QueryName condition="end with">.snapads.com</QueryName>
<QueryName condition="end with">.spotxchange.com</QueryName>
<QueryName condition="end with">.taboola.com</QueryName>
<QueryName condition="end with">.taboola.map.fastly.net</QueryName>
<QueryName condition="end with">.tapad.com</QueryName>
<QueryName condition="end with">.tidaltv.com</QueryName>
<QueryName condition="end with">.trafficmanager.net</QueryName>
<QueryName condition="end with">.tremorhub.com</QueryName>
<QueryName condition="end with">.tribalfusion.com</QueryName>
<QueryName condition="end with">.turn.com</QueryName>
<QueryName condition="end with">.twimg.com</QueryName>
<QueryName condition="end with">.tynt.com</QueryName>
<QueryName condition="end with">.w55c.net</QueryName>
<QueryName condition="end with">.ytimg.com</QueryName>
<QueryName condition="end with">.zorosrv.com</QueryName>
<QueryName condition="is">1rx.io</QueryName>
<QueryName condition="is">adservice.google.com</QueryName>
<QueryName condition="is">ampcid.google.com</QueryName>
<QueryName condition="is">clientservices.googleapis.com</QueryName>
<QueryName condition="is">googleadapis.l.google.com</QueryName>
<QueryName condition="is">imasdk.googleapis.com</QueryName>
<QueryName condition="is">l.google.com</QueryName>
<QueryName condition="is">ml314.com</QueryName>
<QueryName condition="is">mtalk.google.com</QueryName>
<QueryName condition="is">update.googleapis.com</QueryName>
<QueryName condition="is">www.googletagservices.com</QueryName>
<QueryName condition="end with">.mozaws.net</QueryName>
<QueryName condition="end with">.mozilla.com</QueryName>
<QueryName condition="end with">.mozilla.net</QueryName>
<QueryName condition="end with">.mozilla.org</QueryName>
<QueryName condition="is">clients1.google.com</QueryName>
<QueryName condition="is">clients2.google.com</QueryName>
<QueryName condition="is">clients3.google.com</QueryName>
<QueryName condition="is">clients4.google.com</QueryName>
<QueryName condition="is">clients5.google.com</QueryName>
<QueryName condition="is">clients6.google.com</QueryName>
<QueryName condition="is">safebrowsing.googleapis.com</QueryName>
<QueryName condition="end with">.akadns.net</QueryName>
<QueryName condition="end with">.netflix.com</QueryName>
<QueryName condition="end with">.aspnetcdn.com</QueryName>
<QueryName condition="is">ajax.googleapis.com</QueryName>
<QueryName condition="is">cdnjs.cloudflare.com</QueryName>
<QueryName condition="is">fonts.googleapis.com</QueryName>
<QueryName condition="end with">.typekit.net</QueryName>
<QueryName condition="is">cdnjs.cloudflare.com</QueryName>
<QueryName condition="end with">.stackassets.com</QueryName>
<QueryName condition="end with">.steamcontent.com</QueryName>
<QueryName condition="end with">.arpa.</QueryName>
<QueryName condition="end with">.arpa</QueryName>
<QueryName condition="end with">.msftncsi.com</QueryName>
<QueryName condition="end with">.localmachine</QueryName>
<QueryName condition="is">localhost</QueryName>
<Rule groupRelation="and">
<Image condition="is">C:\ProgramData\LogiShrd\LogiOptions\Software\Current\updater.exe</Image>
<QueryName condition="end with">.logitech.com</QueryName>
</Rule>
<Image condition="is">C:\Program Files\Windows Defender Advanced Threat Protection\MsSense.exe</Image>
<QueryName condition="end with">-pushp.svc.ms</QueryName>
<QueryName condition="end with">.b-msedge.net</QueryName>
<QueryName condition="end with">.bing.com</QueryName>
<QueryName condition="end with">.hotmail.com</QueryName>
<QueryName condition="end with">.live.com</QueryName>
<QueryName condition="end with">.live.net</QueryName>
<QueryName condition="end with">.s-microsoft.com</QueryName>
<QueryName condition="end with">.microsoft.com</QueryName>
<QueryName condition="end with">.microsoftonline.com</QueryName>
<QueryName condition="end with">.microsoftstore.com</QueryName>
<QueryName condition="end with">.ms-acdc.office.com</QueryName>
<QueryName condition="end with">.msedge.net</QueryName>
<QueryName condition="end with">.msn.com</QueryName>
<QueryName condition="end with">.msocdn.com</QueryName>
<QueryName condition="end with">.skype.com</QueryName>
<QueryName condition="end with">.skype.net</QueryName>
<QueryName condition="end with">.windows.com</QueryName>
<QueryName condition="end with">.windows.net.nsatc.net</QueryName>
<QueryName condition="end with">.windowsupdate.com</QueryName>
<QueryName condition="end with">.xboxlive.com</QueryName>
<QueryName condition="is">login.windows.net</QueryName>
<QueryName condition="is">outlook.office.com</QueryName>
<QueryName condition="is">statics.teams.cdn.office.net</QueryName>
<QueryName condition="is">acdc-direct.office.com</QueryName>
<QueryName condition="end with">.fp.measure.office.com</QueryName>
<QueryName condition="end with">office365.com</QueryName>
<QueryName condition="end with">.activedirectory.windowsazure.com</QueryName>
<QueryName condition="end with">.aria.microsoft.com</QueryName>
<QueryName condition="end with">.msauth.net</QueryName>
<QueryName condition="end with">.msftauth.net</QueryName>
<QueryName condition="end with">.opinsights.azure.com</QueryName>
<QueryName condition="is">management.azure.com</QueryName>
<QueryName condition="is">outlook.office365.com</QueryName>
<QueryName condition="is">portal.azure.com</QueryName>
<QueryName condition="is">substrate.office.com</QueryName>
<QueryName condition="is">osi.office.net</QueryName>
<QueryName condition="end with">.digicert.com</QueryName>
<QueryName condition="end with">.globalsign.com</QueryName>
<QueryName condition="end with">.globalsign.net</QueryName>
<QueryName condition="is">msocsp.com</QueryName>
<QueryName condition="is">ocsp.msocsp.com</QueryName>
<QueryName condition="is">pki.goog</QueryName>
<QueryName condition="end with">.pki.goog</QueryName>
<QueryName condition="is">ocsp.godaddy.com</QueryName>
<QueryName condition="is">amazontrust.com</QueryName>
<QueryName condition="end with">.amazontrust.com</QueryName>
<QueryName condition="is">ocsp.sectigo.com</QueryName>
<QueryName condition="is">pki-goog.l.google.com</QueryName>
<QueryName condition="end with">.usertrust.com</QueryName>
<QueryName condition="is">ocsp.comodoca.com</QueryName>
<QueryName condition="is">ocsp.verisign.com</QueryName>
<QueryName condition="is">ocsp.entrust.net</QueryName>
<QueryName condition="end with">ocsp.identrust.com</QueryName>
<QueryName condition="is">status.rapidssl.com</QueryName>
<QueryName condition="is">status.thawte.com</QueryName>
<QueryName condition="is">ocsp.int-x3.letsencrypt.org</QueryName>
<QueryName condition="is">subca.ocsp-certum.com</QueryName>
<QueryName condition="is">cscasha2.ocsp-certum.com</QueryName>
<QueryName condition="is">crl.verisign.com</QueryName>
<Image condition="contains all">C:\Program Files\SentinelOne\Sentinel Agent;\SentinelAgent.exe</Image>
<QueryName condition="end with">.spotify.com</QueryName>
<QueryName condition="end with">.spotify.map.fastly.net</QueryName>
<Image condition="contains all">C:\Windows\SystemApps\Microsoft.Windows.Search;SearchApp.exe</Image>
</DnsQuery>
</RuleGroup>
<!-- Event ID 23 == File Delete and overwrite events which saves a copy to the archivedir - Includes -->
<RuleGroup groupRelation="or">
<FileDelete onmatch="include" />
</RuleGroup>
<!-- Event ID 23 == File Delete and overwrite events - Excludes -->
<RuleGroup groupRelation="or">
<FileDelete onmatch="exclude">
<Image condition="contains all">\appdata\local\google\chrome\user data\swreporter\;software_reporter_tool.exe</Image>
<Image condition="is">C:\Program Files (x86)\Google\Chrome\Application\chrome.exe</Image>
<User condition="contains any">NETWORK SERVICE; LOCAL SERVICE</User>
<Rule name="PowerShell Profile Deletion" groupRelation="and">
<TargetFilename condition="contains">AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-Interactive</TargetFilename>
<Image condition="is">C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe</Image>
</Rule>
</FileDelete>
</RuleGroup>
<!-- Event ID 24 == Clipboard change events, only captures text, not files - Includes -->
<RuleGroup groupRelation="or">
<!-- Default set to disabled due to privacy implications and potential data you leave for attackers, enable with care!-->
<ClipboardChange onmatch="include" />
</RuleGroup>
<!-- Event ID 25 == Process tampering events - Excludes -->
<RuleGroup groupRelation="or">
<ProcessTampering onmatch="exclude">
<Image condition="is">C:\Program Files\Mozilla Firefox\firefox.exe</Image>
<Image condition="is">C:\Program Files\Mozilla Firefox\updater.exe</Image>
<Image condition="is">C:\Program Files\Mozilla Firefox\default-browser-agent.exe</Image>
<Image condition="is">C:\Program Files\Mozilla Firefox\pingsender.exe</Image>
<Image condition="is">C:\Program Files\Git\cmd\git.exe</Image>
<Image condition="is">C:\Program Files\Git\mingw64\bin\git.exe</Image>
<Image condition="is">C:\Program Files\Git\mingw64\libexec\git-core\git.exe</Image>
<Image condition="is">C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe</Image>
<Rule groupRelation="and">
<Image condition="begin with">C:\Program Files (x86)\Microsoft\Edge\Application\</Image>
<Image condition="end with">\BHO\ie_to_edge_stub.exe</Image>
</Rule>
<Rule groupRelation="and">
<Image condition="begin with">C:\Program Files (x86)\Microsoft\Edge\Application\</Image>
<Image condition="end with">\identity_helper.exe</Image>
</Rule>
<Rule groupRelation="and">
<Image condition="begin with">C:\Program Files (x86)\Microsoft\EdgeUpdate\Install\</Image>
<Image condition="contains">\MicrosoftEdge_X64_</Image>
</Rule>
<Image condition="contains">unknown process</Image>
<Image condition="is">C:\Program Files\Microsoft VS Code\Code.exe</Image>
</ProcessTampering>
</RuleGroup>
<!-- Event ID 26 == File Delete and overwrite events - Excludes -->
<RuleGroup groupRelation="or">
<FileDeleteDetected onmatch="exclude">
<Image condition="contains all">\appdata\local\google\chrome\user data\swreporter\;software_reporter_tool.exe</Image>
<Image condition="is">C:\Program Files (x86)\Google\Chrome\Application\chrome.exe</Image>
<User condition="contains any">NETWORK SERVICE; LOCAL SERVICE</User>
</FileDeleteDetected>
</RuleGroup>
</EventFiltering>
</Sysmon>
